As the internet is becoming increasingly present and relevant to business and professional activities, questions increase how to maintain privacy and security on the web so that it does not harm business. Storing personal, private and financial information from the company and keeping it protected may be difficult, but it is possible to avoid the vast majority of scams, spyware and privacy violations.
Therefore, we have elaborated some tips for you to know if your company's internet is being used correctly by employees, avoiding threats, or if it is free for possible virtual attacks .
SITE SAFETY VERIFICATION
Many times your employees may be surfing the internet for something, or just passing time if there is a internet use policy and migrating from site on site. This type of behavior can be harmful to the company, taking into account safety. Since today there is a multitude of websites available for access, if safety and reliability is not verified, it is easy to fall into a trap.
Some sites request personal information to connect to your account or to complete a transaction. Spyware hackers, thieves and programmers know this, and often try to intercept their information during these transactions. Therefore, always use secure websites and companies and require access rules to be properly fulfilled by your team.
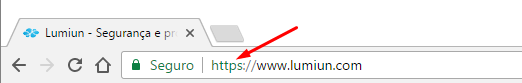
Firstly, your information should only be delivered to respected companies, and then make sure the company's website uses a web address that starts with "https" and has a lock symbol in the address bar or the bottom of the browser. This means that the site encrypts your information by virtually render the data to any thief or hacker that can intercept the transmission.
Nothing is free
Are you full of good people on the internet wanting to offer wonderful and undeniable gifts and offers? Rarely. Many times a tempting contesting contest on social networks with the draw of various technology products or even ads for you to receive gifts or gifts at home.
You need to be aware of this type of campaign, as most of these promotions asks you to fill out a registration with personal data to be able to compete. These contests often cheer up people, so in the workplace can be important to be aware of what employees access, so that they do not end up putting sensitive data from the company at risk.
Cybercriminals use these attacks to collect information that can be used in identity theft attacks. It is important to know that these hackers are all the time looking for something, in case no network to infect.
There is also ransomware, which is a type of malware (malware) to block access to files or systems to only release them after payment of a specified value. It's like a kidnapping, but virtual. Although they are seen as a recent security problem, ransomware is not a new concept: the first references to this type of digital plague refer to the late 1980s.
Qualified passwords
Most people use easy passwords to memorize, or reminiscent of dates such as birth, someone's birthday, or numbers such as "123456". Most of the time it is not the best option. From email to social networks, passing the internet banking. Passwords are an essential component of our life on the internet. Passwords should protect our unnatched access information. The stronger the password, it is harder to break.
This concern for qualified passwords needs to come from all employees, not only those who access the most important information, such as bank data. In a Splashdata , it was noticed that many people used easy and very dangerous passwords in 2016. Know what were the 25 most used passwords in the world in 2016 . If you want to protect yourself more properly, using safe and stronger passwords, you can check out our guide for creating and management of User and Safe Passwords . With it you will know a set of rules and actions to create and manage passwords in the best way, reducing the chance that are discovered and consequently attacks and threats.
Identify fake emails
E-mails saying you have a debt with a telephone company or stating that one of your documents is illegal, or even, the message offers you awards or virtual love cards? Intimate you for a judicial audience? Contains a supposed important news about a famous personality? It is likely to be a spam , that is, a fake email.
If the message has texts with spelling and grammatical errors, make tempting offers or have a different link from the indicated (to check the true link, just get the mouse over it, but without clicking), be suspicious immediately. When in doubt, contact the company whose name was involved in the email.
In using corporate email, it is important to take extra care, because employees can often open a spam email even without knowing, simply because it “seems” contains something important. In this case inform or give some tips, such as taking care of the sender, may be important.
Update of programs
It is also important to keep your company programs up to date. Many people think that new versions only add resources, but the truth is that they also have corrections for safety failures. Therefore, always use the latest version of your programs, especially those who access the internet (internet browsers, email customers, etc.). Many apps have a functionality that updates the program automatically or warns of the launch of new versions. It is a good habit to leave this feature activated.
Has some type of monitoring or security software
It is a great option for those who are willing to invest money in search of controlling threats and keeping the network safer. Companies that work with important data and are unable to monitor each company employee, can opt for internet control . This type of solution helps the network is more protected, and maintains control of what each employee is accessing within the business network. With this the owner can manage and know if the employee is not accessing harmful sites that may harm or put the company at risk.
Practice any of the tips mentioned above. Share your experience with us and wait for more security tips on the internet!












3 Comments
Comments closed