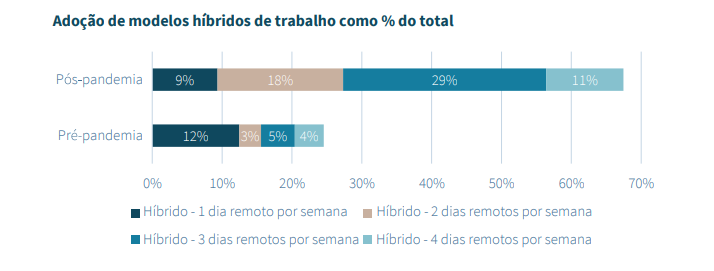
Hybrid work, a model that combines face -to -face and remote activities, has grown exponentially in recent years. Brazil stands out with 45% of companies operating under this regime. However, this flexibility brings significant challenges for digital security, requiring new data protection approaches.
With increasing remote work, attempts at cyber attacks have also grown . In 2024, Brazil recorded impressive 356 billion attempts at attacks . These numbers reveal the hidden risks of hybrid work, raising the question: Is your team really safe working from home? Discover the invisible risks and how to avoid them.
The impact of hybrid work on the digital safety of companies
The hybrid work model has been consolidated in Brazil, with 61.8% of companies planning to maintain this practice permanently, according to research by Anywhere Office: new models of work in the postpandeia world , KPMG.
However, this flexibility brings significant challenges to digital security as employees access corporate systems from often less secure home networks.
In 2024 , Brazil registered a 67% increase in cybership during the second quarter, with an average of 2,754 weekly attempts .
In addition, the country emerged as the fourth in Latin America with the largest number of cyber threats in the first half of 2024 , representing 7.76% of the total detected in the region.
These data show the growing cyber threat in the context of hybrid work, requiring companies to reinforce their security measures to protect sensitive data and ensure the integrity of their systems.
Increased attempts at remote attacks
The number of cyber attacks has grown significantly. According to data published at Tecmundo da Fortiguard Labs , Brazil recorded 356 billion attempts at cyber attacks in 2024, leading the list in Latin America, followed by Mexico, Colomba and Peru.
This growth reflects the growing vulnerability of home networks and the lack of adequate safety infrastructure in many companies.
These data therefore reinforce the urgency of implementing robust digital security strategies. In addition, the use of internet access control solutions, such as content filter systems, can block access to malicious websites, preventing employees, often vulnerable to their home networks, from connecting to harmful sources.
In addition, next -generation firewalls are essential for inspecting and filtering data traffic between the corporate network and the external environment, identifying suspicious behaviors and mitigating the risk of attacks. The use of VPNs ensures that communications between remote employees and internal systems are encrypted, making it difficult to intercept sensitive data. To maximize safety, the implementation of multifactorial authentication (MFA), which requires multiple forms of verification before giving access to critical systems, is essential.
Challenges in IT management
Ensuring that all employees follow security protocols, even without face -to -face supervision, is one of the main challenges of IT management in hybrid work. With the diversity of environments where employees operate, whether at home, cafes or other public places, it is more difficult to maintain control over security measures. According to research, 60% of companies consider data security as one of the biggest challenges in managing remote endpoints. In addition, 55% of IT leaders point out the difficulty in keeping updated software installed on remote devices as a significant obstacle.
To mitigate these risks, it is essential that companies implement clear and well -defined security policies . These guidelines should address the use of personal devices, access to sensitive data, and navigation on unreliable networks. Remote monitoring tools such as IDS Detection Systems (IDS) and mobile management software (MDM) are fundamental to ensure data protection even outside the corporate environment.
In addition, continuous education of employees is vital. Offering regular cybersecurity training and conducting incident simulations can help increase threat awareness. By educating employees, companies significantly reduce the risk of attacks, as security practices become everyone's responsibility.
The main risks of safety in hybrid work
As hybrid work becomes the norm for many companies, digital safety risks amplify, mainly due to increasing dependence on external devices and networks. The hybrid model provides flexibility, but also creates significant vulnerabilities that organizations need to face. Check Point Software report in 2024, more than 70% of infected devices were personal, with attackers to “bring their own device” (BYOD) to violate corporate resources. This statistics reflects the urgency with which organizations need to protect their systems and data.
One of the main risks, therefore, is in the use of non-secure Wi-Fi networks , common in domestic or public environments. In addition, Man-in-the-Middle (MITM) are frequent in these networks, where data can be intercepted.
Finally, the risk of committed credentials is exacerbated by hybrid work. Without direct supervision, it is easier for employees to adopt insecure practices, such as the use of weak passwords or credential sharing. Verizon report , credential commitment was the most common method for violating networks, being the initial access vector in 38% of all data violations. This makes the protection of digital identities even more important in a remote environment, where constant vigilance becomes more difficult. To mitigate these risks, it is essential for companies to implement clear safety policies and robust access control tools.
Use of non-secure Wi-Fi networks
The growing dependence on Wi-Fi networks for hybrid work connectivity increases companies exposure to significant digital safety risks. Connecting to non-protected public or domestic Wi-Fi networks becomes a vulnerable point, especially when sensitive data, such as passwords and bank information, are transmitted. In a global study, Kaspersky found that 25% of Wi-Fi networks in the world had no encryption or password protection.
DNS Spoofing attacks , where hackers deceive devices to connect to counterfeit servers. As a result these attacks redirect the victim to malicious websites that collect their confidential information.
To mitigate these risks, it is essential for companies to educate their employees about the importance of avoiding public networks to access corporate systems. VPNs (virtual private networks) are an effective solution as they encrypt the data transmitted, making it inaccessible to hackers. In addition, configuring firewalls and ensuring that housewords are protected with strong passwords and WPA3 encryption helps significantly reduce the chances of data interception.
Personal devices vs. corporate devices
The use of work devices BYOD (Bring Your Own Device) , is increasingly common in the hybrid work model. However, this practice may pose a significant risk to the company's safety if devices are not properly managed. Many personal devices do not have the necessary safety measures , such as updated antivirus software , configured firewalls , or access control policies implemented, making them easy for cybercriminals.
In addition, personal devices often do not follow corporate safety standards and may not be configured to effectively protect sensitive data. This increases the chances that access credentials, confidential documents and other essential information are exposed in case of security failures. In 2024 alone there was a 44% increase in cyber attacks worldwide last year, according to Annual Security Report, The State of Global Cyber Security 2024 .
On the other hand, corporate devices , when properly configured and managed by the IT team, offer a higher level of security. These devices can be protected by corporate safety software such as antiviruses and specific safety modules access and authentication policies are followed. The use of MFile Device Management (MDM) , for example, allows the company to remotely control devices settings, implementing blockages, erasing data in case of loss and applying safety updates automatically, which considerably reduces risks.
Lack of control over accesses and permissions
Lack of control over access and permissions is one of the main failures of safety in hybrid work. Without an effective system, sensitive data such as financial documents and customer information, they can be exposed improperly. This occurs when credentials are shared, poorly managed or committed to attacks such as Phishing and Brute Force .
With remote work, the risks increase as more devices access the corporate network. If permissions are not well configured, confidential information may fall to the wrong hands. An example was the Target attack , which exposed 40 million credit cards due to inadequate credential control.
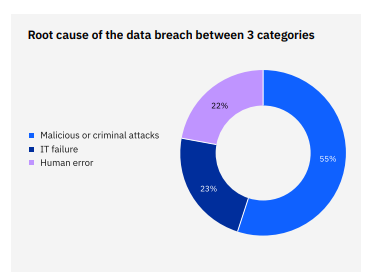
In addition, 22% of security incidents occur by human error , such as failures in the configuration of access and improper sharing of credentials.
To reduce these risks, it is essential to implement an Identity and Access Management System (AMI) and use Multifatorial Authentication (MFA). According to Microsoft (2024), MFA can block 99.9% of credential commitment attacks, becoming a key barrier to corporate security.
Social engineering and targeted attacks
Social engineering attacks such as phishing are one of the biggest threats in the hybrid work environment. With the increase in remote work, cyber criminals exploit the distance from the teams to apply more sophisticated blows. Using fraudulent emails or text messages, they are undergoing colleagues, supervisors or service providers to steal login credentials or induce employees clicking on malicious links.
According to the IBM 2024 data violations report , Phishing accounted for 15% of violations and cost an average of US $ 4.88 million per incident . The use of committed credentials facilitated 16% of violations, with an average cost of US $ 4.81 million .
These attacks are even more dangerous because they exploit information from social networks and previous interactions to deceive the victims. In addition, when passing by authority figures, criminals increase the chance of success, inducing employees to share sensitive data or download malicious files.
The human factor is one of the main facilitators of this type of scam. Without constant supervision, employees can click on links or download attachments without realizing the risks. In addition, physical distance reduces the ability to identify signs of fraud, such as an unusual tone in an email or suspicious orders.
To mitigate these risks, it is essential to invest in regular cyber security training , focused on identifying scams. In addition, using email filters and link checks can dramatically reduce the impact of these attacks, strengthening the safety of corporate information.
Good practices to protect data in hybrid work
Protecting data in the hybrid work environment requires the adoption of good practices that ensure safety in both the physical and digital location. One of the main strategies is the implementation of secure connections , such as the use of VPNs (virtual private networks) , which encrypt communication between employees and corporate network, preventing sensitive data from being intercepted. By using a VPN, employees can access company information safely, even when connected to public or domestic networks, reducing the risk of Man-in-the-Middle attacks and data interception .
In addition, Multifator Authentication (MFA) is essential to strengthen security. MFA requires users to provide two or more authentication factors (such as a password and a code sent to mobile) before accessing corporate systems or data. This makes it difficult for attackers to access employees' accounts, even if they can get a compromised password.
Another important aspect to protect data is access and permissions management Identity Management and Access (AMI) system . With this, it is possible to ensure that only authorized employees can access data and critical systems. In addition, establish clear cyber security policies such as the use of strong passwords , restrictions on personal devices and constant monitoring of networks and systems are essential for protection. Finally, employee continuous education on best security practices helps create a safety culture within the organization, minimizing risks and promoting a safer work environment for all.
Implementation of secure connections
Data safety at hybrid work depends on the use of VPNs, secure wi-fi networks and firewalls.
VPNs, in turn, create an encrypted tunnel that protects traffic between devices and corporate servers, preventing the interception of credentials, data and files by hackers. This, therefore, is critical for employees who access public networks, such as cafes and airport Wi-Fi, reducing risks such as Man-in-The-Middle attacks.
In addition, the safety of employees' household Wi-Fi networks is essential. It is essential to use strong passwords and WPA3 authentication, which offers more advanced encryption than WPA2, making it difficult to invasions and brute strength attacks.
Firewalls are also indispensable. They monitor traffic, block suspicious connections, and help detect malicious activities.
The combination of VPNs, safe wi-fi and firewall networks creates a robust defense against cyber threats, protecting corporate data without compromising remote work flexibility.
Use of Multifator Authentication (MFA)
With increasingly sophisticated attacks, Multifator Authentication (MFA) has become essential, requiring at least two ways of verifying systems and applications. This may include password, smartphone code or biometrics .
The MFA makes invasions difficult, because even if a criminal steals a password, it will still need to get around another barrier. In addition, companies that adopt this technology strengthen their security, protecting sensitive data and increasing the trust of employees and partners.
For greater protection, MFA can be configured with apps like Google Authenticator and Microsoft Authenticator or biometric authentication. This is especially important in hybrid work, where the risks of external attacks are even greater.
Security and access security policies
In the hybrid work environment, where many employees use personal devices to access corporate systems, clear safety policies are essential to protect data and ensure continuity of operations. These policies should include requirements for strong passwords , such as fighter combinations, numbers and special characters, as well as the obligation of regular software updates , which helps to correct vulnerabilities and reduce risks of attacks. Permissions management plays a key role, limiting access to sensitive data and ensuring that only authorized users can access critical information.
The implementation of an Identity and Access Management System (AMI) , along with multifactorial authentication (MFA) , strengthens safety, making unauthorized access difficult, even if credentials are compromised. According to the IBM 2024 data violation costs report , committed credential attacks represented 16% of data violations, highlighting the importance of these protection measures.
In addition, it is vital to create clear rules on the use of personal devices (BYOD), which, while a common practice, can expose the company to risk if they are not accompanied by strict security measures. The installation of antivirus, firewalls and sensitive data cryptography are indispensable actions to protect corporate information. With well -implemented security policies, companies not only protect their data, but promote a digital security culture among employees, whether in the office or home office.
Backup and data recovery at hybrid work
In the hybrid work environment, where employees access remote corporate data, protecting and recovering information becomes essential. Automating cloud backups offers extra safety by protecting data from physical and cyber threats such as ransomware. The cloud also offers scalability and storage flexibility, ensuring data integrity without increasing costs. On average, 41% of production data is affected by attacks , and only 51% are recoverable , according to the Veeam report .
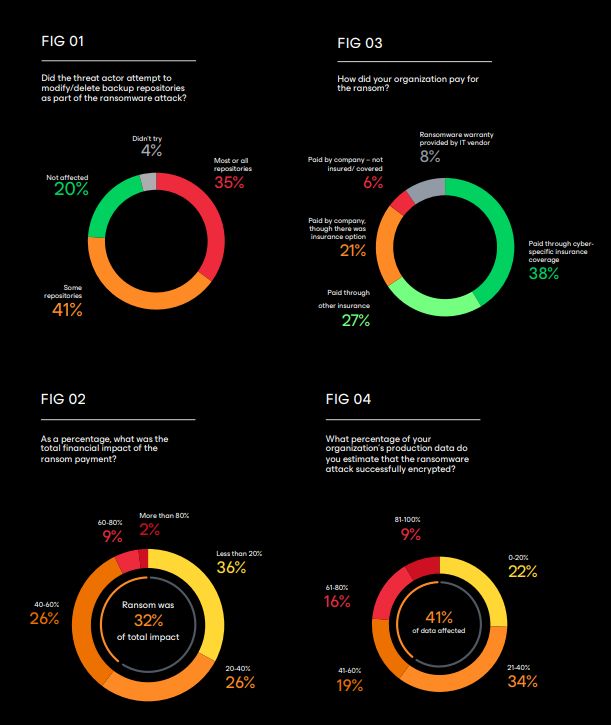
In addition to backup, it is essential to test recovery processes to ensure that data can be restored quickly in case of failures or attacks. Otherwise, without regular tests, companies can find out too late that their backups do not work as expected.
Finally, it is necessary to integrate backup solutions with clear data retention policies , according to regulations such as General Data Protection Regular ( GDPR ) or General Data Protection Law ( LGPD ) . Non -compliance can result in penalties and loss of customer confidence. A solid backup and recovery strategy ensures continuity of operations, even in the face of unforeseen incidents.
Employee Training and Awareness
In the current scenario of cybersecurity, employees play a key role in protecting digital threats. Studies indicate that 95% of cyber security failures result from human errors , such as clicks on malicious links or confidential information on phishing attacks. Investing in regular digital security training is essential to enabling employees to recognize and avoid these threats.
These training should include from creating strong passwords and the importance of multifactorial authentication to practical attack simulations such as phishing and ransomware . Conducting simulations allows employees to practice incident responses without real consequences, making learning more effective. In addition, it is essential to address new trends and constantly evolving attacks, such as targeted attacks and social engineering. Familiate employees with real examples, such as Cognizant's ransomware attack in 2020 , contributes to a more robust security culture.
With continuous awareness and effective training, companies can significantly reduce the number of safety incidents, establishing a more solid defense against cyber attacks. In addition, constant education in digital security is a strategic practice that protects financial resources and organizational reputation.
Essential tools to ensure safety at hybrid work
With the advancement of hybrid work, digital safety has become fundamental as employees access corporate systems from various locations and devices. To protect digital infrastructure, it is essential to adopt effective solutions.
Advanced firewalls are fundamental to prevent unauthorized access and targeted attacks, ensuring the safety of communication between remote devices and corporate servers. Household nets need protection as many connections occur via residential Wi-Fi. The use of VPNs strengthens this security by encrypting data and avoiding interceptions.
Mobile Device Management ( MDM) allows companies to apply security policies such as encryption and strong authentication, reducing data leakage risks.
Solutions such as Lumiun Box and Lumiun DNS help reinforce these protective layers by controlling network traffic and blocking unwanted access. Investing in these technologies is essential to ensure a safe and efficient hybrid environment.
Safety solutions for networks and devices
With the growth of hybrid work, the safety of networks and devices has become a critical challenge. Remote access to sensitive data and corporate systems requires effective solutions to prevent cyber threats.
Firewalls are essential for protecting networks, acting as a barrier against unauthorized access and cyber attacks such as DDOS.
Antiviruses and antimalware are indispensable for protecting devices, especially from home networks or public Wi-Fi. Performing regular updates is critical to combating new threats and maintaining protection up to date.
Real -time traffic monitoring is a vital strategy to identify suspicious activities quickly. Real -time traffic monitoring is a vital strategy to identify suspicious activities quickly. In addition, Internet access control solutions, such as blocking unwanted websites and restriction to malicious content, are essential to strengthen digital security and reduce the risk of cyber attacks.
Mobile Device Management cloud -based solutions offer centralized control, ensuring safety policies, encryption and advanced protection.
Keeping updated safety tools and adopting a layer defense are important practices for protecting data and ensuring business continuity in hybrid environments.
Access control and password management
Access control and password management are fundamental to protecting company sensitive information, especially in a hybrid work environment. With increasing dependence on digital systems and applications, ensuring that only authorized persons can access certain data is a priority.
Trends in Identity Security 2024 report , 84% of organizations that suffered an identity -based violations last year reported direct business impacts , a significant increase over 68% by 2023.
To reduce these risks, credential management platforms simplify the creation, storage and monitoring of passwords, encouraging the use of strong and unique combinations. Password vaults) offer safe and encrypted storage, allowing controlled sharing without exposing credentials in clear text.
In addition, Identity Management and Access Systems (AMI) increase security by defining detailed permissions, recording activities and conducting audits. The adoption of these practices strengthens corporate protection, reducing vulnerabilities and ensuring business continuity.
Monitoring and response to incidents
Continuous monitoring of networks and devices is essential to detect and respond to real -time threats, especially in hybrid work. With increasingly sophisticated attacks, early detection avoids significant damage to company systems.
Solutions such as network monitoring, intrusion detection (IDS) and User Behavior Analysis (UBA) identify suspicious activities before serious attacks become. These tools analyze traffic, access and interactions, alerting safety teams on abnormal behaviors.
In addition, a quick response to incidents is critical. A incident response (IRP) plan allows you to contain threats, correct vulnerabilities, and restore system safety. The plan should define protocols for different types of attacks, such as data leaks and ransomware, as well as including regular training, automated simulations and tools to increase the effectiveness of the response.
The implementation of these practices minimizes impacts and strengthens the protection of the company's assets , reducing risks and ensuring greater safety in the digital environment.
Conclusion: Digital protection at hybrid work: a continuous commitment
Digital safety at hybrid work is not an isolated action, but a continuous process that requires technology, effective policies and employee awareness . In an increasingly digital environment, where the remote and face -to -face mix, the protection of corporate data requires an integrated approach.
adoption , secure connections, firewalls, proper password management and internet access control solutions are essential steps to mitigate risks such as phishing, ransomware and improper access . However, the first line of defense is the employee himself . Regular training ensures that the team is prepared to identify threats and act correctly.
In addition, the integration of centralized safety solutions , with real -time monitoring and rapid response to incidents , reduces impacts and strengthens the resilience of the company.
Finally, protecting data should be a commitment from the entire organization , from high management to employees. Companies that prioritize digital security not only avoid damage but gain a competitive advantage in the market.









