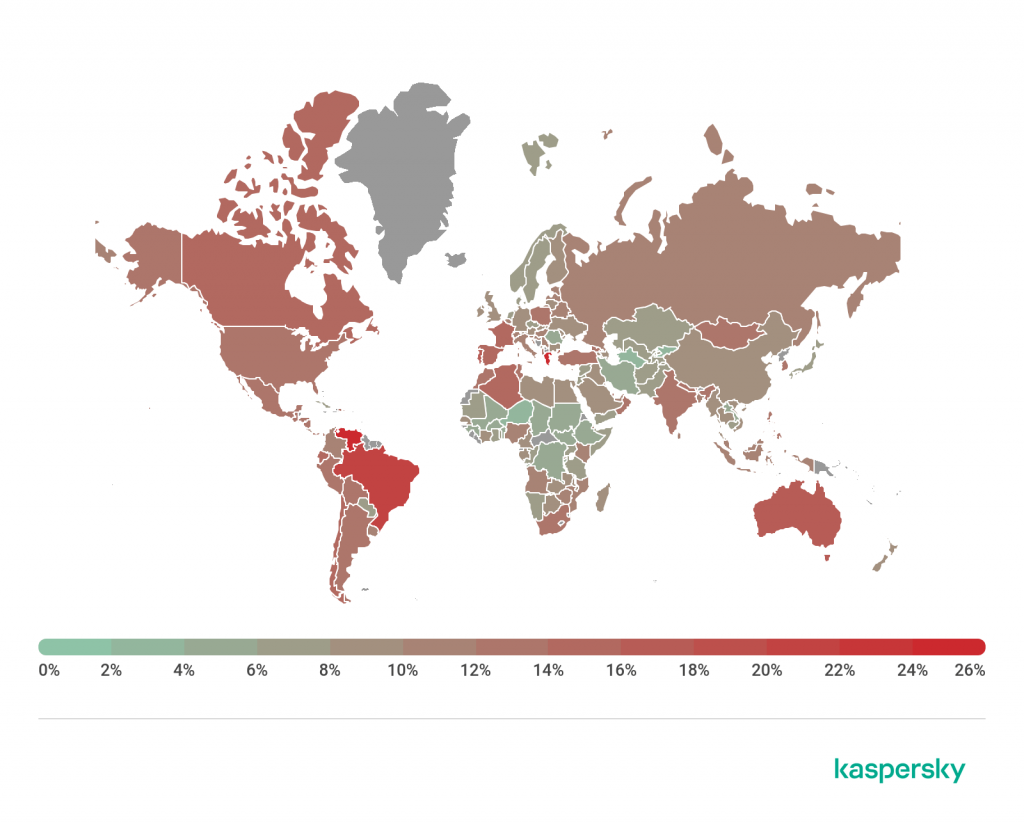
The volume of phishing attacks targets people and companies in Brazil is still very high: out of 5 Brazilian users, 1 is susceptible to phishing . Brazil is in the 3rd position of the ranking of the most attacked countries by phishing blows .
A report published by Cisco in 2019 pointed out that 38% of respondents faced problems with phishing last year.
A phishing story
A usual Facebook user sees on his feed an ad from a Samsung 4K 58 ″ TV for $ 999.00. Unmissable price. Americanas from Americanas. Nor does it consider whether the announcement is from Americanas, because the colors, the logo, the writings, are from Americanas, he already knows. And the ad is broadcast by Facebook. So there is no time to lose, with this price soon will have no more stock. In addition to a 58 -inch TV, it will also be pleased to have done a great deal. A must -see opportunity. This analysis all takes less than 5 seconds.
The user clicks on the ad and is now on the Americanas website. Again, don't think about assessing if the site is from Americanas, because the colors, logo, everything is exactly as he already knows. The address of this site is https: //www37.sucessodevendason*.com/tkn3025574/smart-tv-led-58-samsung-58m6120-ultra-hd-4k […] but that passes beaten. Maybe he saw the HTTPS lock and felt security. Blind imagining this TV in your home, concludes the purchase, informs the delivery address - anxiety is already beating - and generates the ticket. In the ticket is the beneficiary “Americanas.com - B2W Digital Company”. Show. Then he opens the bank's application, pays the ticket and now the concern comes: how to control anxiety until the time time touches the wonderful order at your door.
Well, this time will not arrive.
This user fell into a phishing blow
Unfortunately he had no attention to some aspects:
- Promotion with very unusual price . I could have researched on Google and sites like Zoom.com which are reasonable price ranges for that product.
- The address of the site that opened when you clicked on the ad . The domain that appeared in the browser's address bar had nothing to do with Americanas.com. This is a great evidence of fraud.
- The name of the bill of the ticket displayed by the bank system before completing the payment . Prior to payment, the bank informs the real beneficiary of the registered ticket, and certainly was not Americanas or B2W (e-commerce group integrated by Americanas).
- Phishing protection technology . A security filter against phishing sites acts as real -time protection for this type of internet threat. If there were on your computer, on your mobile, or in that entire network, a phishing protection mechanism, access to the fraudulent site would likely been blocked - despite the user's inattention as it fell into the blow.
What is phishing
Phishing is a type of cyber crime that consists of misleading internet users , through counterfeit messages and websites, to steal sensitive information such as access passwords and credit card data, and in some cases induce the payment of fraudulent slips .
The most common phishing mode starts with a counterfeit content email, going through a well-known company and inducing the user to click links that direct to the falsified site where the scam is completed. In many cases SMS messages are also used. There are currently even more elaborate campaigns that, instead of email or SMS, transmit the "bait" to users through paid advertisements on social networks. The goal is always to deceive the user, using social engineering and passing on to someone else or another company, so that the user improperly provides confidential data or send payments .
Jesse Burns, Google Cloud Security Technical Director, said in a October 2019 article for the Forbes website, which no one can recognize with full consistency if a web address (URL) is safe to be clicked . Even security experts cannot distinguish with full confidence false pages. Just a little tiredness or stress and anyone can become a victim. According to him, phishing protection needs technology , as it is not enough just to train people.
The term phishing is an adaptation of the English word Fishing , which means fishing.
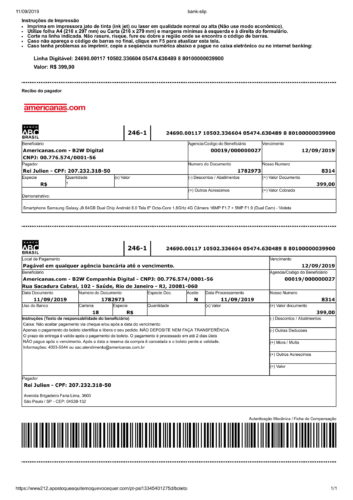
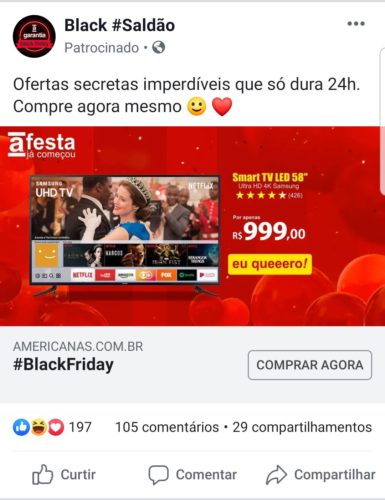
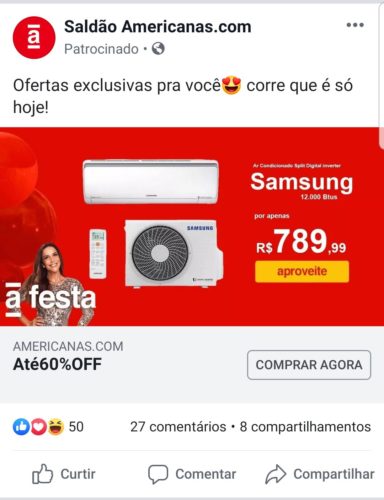
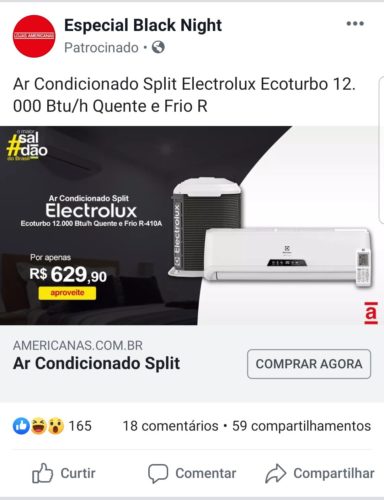
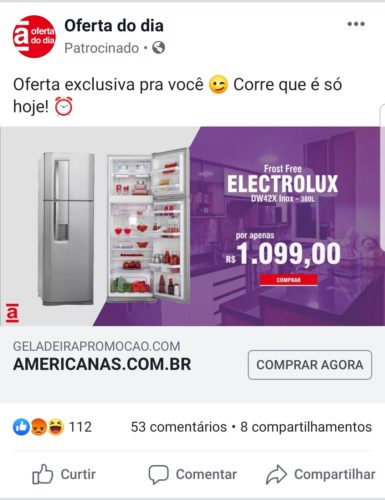
Examples of fraudulent ads on Facebook
You can click on the images to view in a new tab.
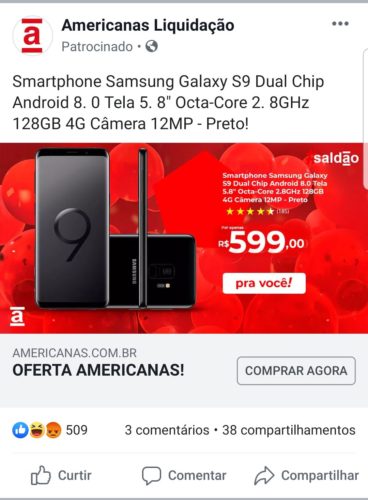
Step by step falling into the blow and buying a smartphone
- Fraudulent advertisement on Facebook, offering a smartphone for a price much lower than normal.
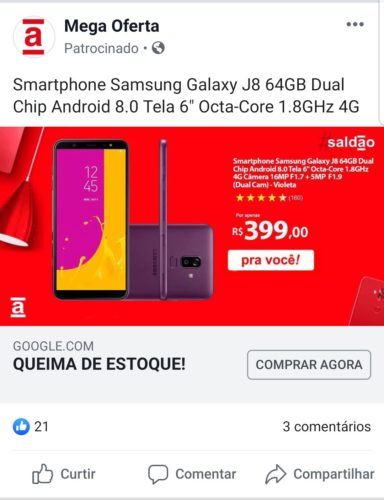
- After clicking on the ad, user is directed to a “fake” e -commerce site, which perfectly mimics the Americanas website. Note that the site address is another.
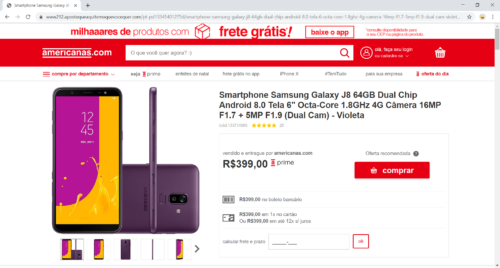
- Clicking on buy, the product already displays in the e-commerce shopping cart.
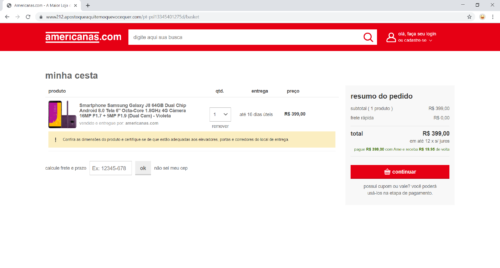
- Advancing the purchase, the fraudulent site requests registration data from the user.
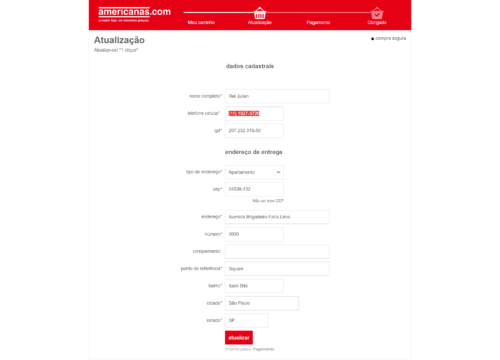
- The site asks the user to choose payment method. In this example, a ticket was selected.
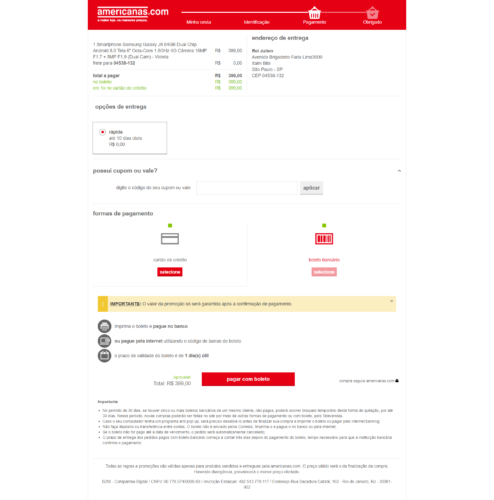
- After generating the ticket, the fake site displays confirmation of the purchase, simulating the operation of the real site.
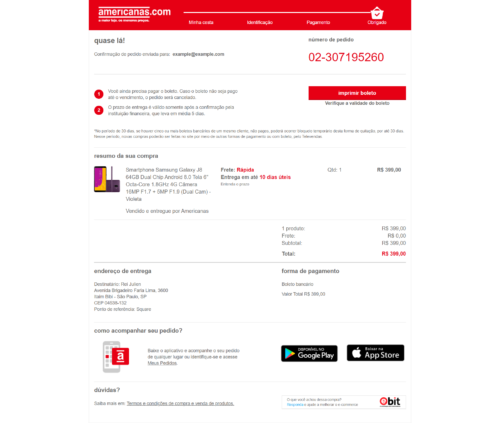
- Fraudulent ticket that was generated on the phishing site. Note that the beneficiary field is “Americanas.com - B2W Digital Company” to deceive the user.
How to avoid phishing blows?
Phishing protection is based on two main elements: user attention to detect fraud evidence; and Phishing protection technology.
The internet user must be responsible for keeping their personal data protected as well as company data and information. The company's manager is responsible for educating employees for good information security practices, as well as determining the implementation of technological resources for network protection.
Attention to what the message or ad is offering or requesting
Be wary of emails, SMS or ads with product offerings at prices far below normal. If in doubt, search the normal price of products on Google or sites like Zoom.com.br. Do not believe in offers sent with incredibly low price. Likewise, don't believe in emails that you ask you to respond with your webmail or bank password-for a supposed update you need to keep your account active-this is fraud. Messages allegedly sent by the IRS informing about irregularity in the CPF are also fraudulent. Be wary of emails allegedly sent by the bank with link to update the Banking Internet module. Do not believe in e-mails with budgets, invoices or service orders you have never requested. And pay attention to the text of the message, it is very common for phishing messages to contain spelling errors.
Attention to the sender and the links contained in the messages
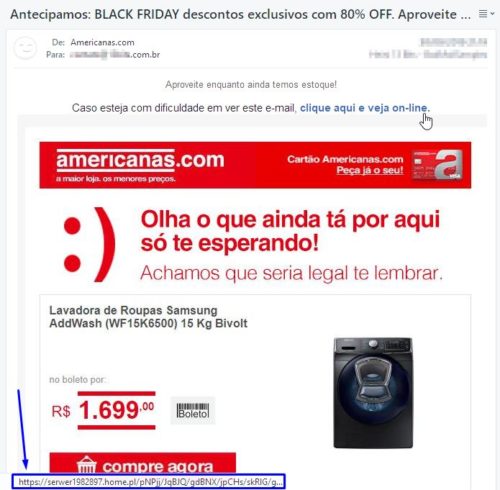
Note carefully to the sender's email address and also the destination address of the links contained in the message. If they are strange, such as “https: //serwer1982897.home*.pl/pnpjj/ […]” In an email allegedly sent by Americans, be wary immediately.
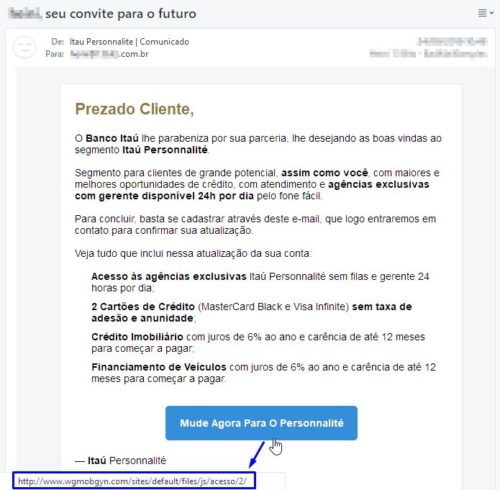
WARNING TO SITE ADDRESS
If you have clicked on a link or ad and have been directed to a site containing a product to buy, a download file or a form requesting data, pay close attention to the address that appears in the browser address bar . That tip to check if the site has the https (encryption) lock is no longer enough, as new phishing sites also use https. However, it is important to analyze whether the site address is correct. When in doubt, go to Google and search the name of the company you want to access. For example, the Americanas website has the address https://www.americas.com.br and it would not be acceptable to use an alleged Americanas website at addresses such as https: //www242.ofertaexclusivadia-liquida*.com, https: //www217.vai-rolar-festa-confira-as-vivities, https: //geladeiraPromocao*.com or https: //www212.ApostoqueAquitoquevocequer*.com (*placed to invalidate the harmful links here in the article).
PHISING SAFETY AND PROTECTION TECHNOLOGY
It is important to use antivirus on the computer. In the case of companies, it is increasingly relevant to also use systems such as firewall and internet access control applied throughout the company's network, regardless of the devices connected to the internal network. This adds a complementary safety layer, which reduces the risk of leakage and loss of information from the company and data from customers and employees, avoiding large inconvenience and financial losses. Through an Internet access control solution , you can also define which site category can be accessed by each user, avoiding waste with work scope and also access to addresses with harmful content. Through this tool, the manager protects the network against sites used in phishing, malware and ransomware .
In the video below we demonstrate the operation of an email phishing, which is passed by the PagSeguro payment service to steal the victim's access data. First is demonstrated access to the non -protective phishing site. Then an attempt is demonstrated to access the phishing site but with the protection of Lumiun active in the company's network.
In this way, the video has a comparison of the effectiveness of a phishing attack on a unprotected network and one with safety and protection technology.
If you have an additional phishing tip or want to clarify any questions, leave your comment here in the article or write me directly at alex@lumiun.com.












12 Comments
Comments closed