If you don't know what phishing is, just think about the number of unsolicited emails you've received. Some informing you that you urgently need to update your account details, others informing you that your access data has been compromised, or that you have won an incredible prize in a promotion that you didn't even participate in. All of this content can be traps, and you need phishing protection features to keep your data safe.
This scam has the following main objectives:
- Obtain confidential data and information fraudulently;
- Access networks and devices;
- Use this data to carry out financial scams.
Through phishing scams, cybercriminals are able to make users provide data unknowingly by clicking on banners, links and other traps. For this reason, it is very important to have a phishing protection tool that helps keep confidential data safer in your company.
Phishing: what are hackers' new strategies?
As seen previously, there are countless ways to carry out a phishing scam , some more easily identifiable than others. As this scam can be applied in different ways, it is necessary to be aware of some factors , such as:
- Be wary of matters considered urgent: it is very common for cybercriminals to use the urgency strategy to make the user access links or download malicious attachments.
- Account compromised: If you receive an email from a bank informing you that your account has been compromised, do not access the link sent. The best alternative is to contact the institution directly to check if there really is a problem with your account.
- E-mails with suspicious attachments deserve extra attention: suspicious attachments (such as invoices, photos, transaction receipts, etc.) must be observed carefully. Hackers often create fake pages very similar to the original ones so that users get confused and end up handing over their access data and credit card information.
Currently, cybercriminals are using new strategies to increase the reach and chances of scams against people and companies. An example of this is Spear Phishing, a strategy where phishing is specifically applied to a group of people such as: managers, company directors, administrators and CEOs.
Another scam that has been causing a lot of damage is BitB Phishing. Want to know how it works? Check out this video that will explain everything you need to know:
It's important to remember that even though this type of attack doesn't always install viruses or malware on devices , it can still pose a big problem. In addition to running the risk of having their confidential information disclosed, companies may also have their activities interrupted, their services made unavailable and suffer substantial financial blows.
Using the vulnerability of employees, cybercriminals gain access to a company's networks and devices, putting business continuity and integrity at risk . To make these scams even more effective, criminals try to make the email subject more attractive , using names from the victim's contact list, companies or financial institutions.
With the advancement of technology, the ways of applying these scams have also advanced, such as:
- Cryptocurrency scam: using messages requesting donations to Ukrainian victims of the recent war against Russia , cybercriminals are able to collect data and obtain cryptocurrencies fraudulently.
- Social media platforms: With the increase in popularity of social media platforms, hackers have used this opportunity to create fake accounts for well-known companies , so that users end up clicking on malicious links and providing their information, especially credit card information.
How could your business be harmed?
Phishing is much more than just a joke to deceive users, it is a scam that can bring several losses to a company , such as:
- Submitting personal and confidential information on false pages or links;
- Contamination of devices by malware, viruses, spyware or ransomware, which is an information hijacking scam that can cause a lot of financial losses;
- Conversion of company computers into bots (zombie computers are often used in DDoS attacks);
- Indiscriminate sending of spam emails to customers and company employees;
- Impact of the company's image on the market;
- Damage to customer relationships;
- Access to confidential data and documents in cloud services;
- Substantial financial scams;
- And many other problems.
Is it possible to avoid accessing phishing websites?
Every day cybercriminals try to develop new techniques to make their strategies deliver results and their malicious links and files are accessed. In this sense, controlling internet access is essential to keep the company protected.
It is very common for employees to use their working time to access entertainment websites, personal emails, social networks and e-commerce, among other content. Although it may seem harmless, this type of attack can cause the user to access malicious links and compromise the security of information within the company, in addition to harming business productivity.
An example of this type of approach is false advertising within the Instagram and Facebook platforms. Cybercriminals create fake profiles identical to those of large companies , such as Americanas, Magazine Luiza, Amazon, and other stores.
Using paid advertisements, they cause promotions to be disseminated to a large volume of people, containing malicious links or fake shopping sites, which cause the user to provide credit card information or pay invoices, suffering substantial financial scams . See an example of this type of scam:
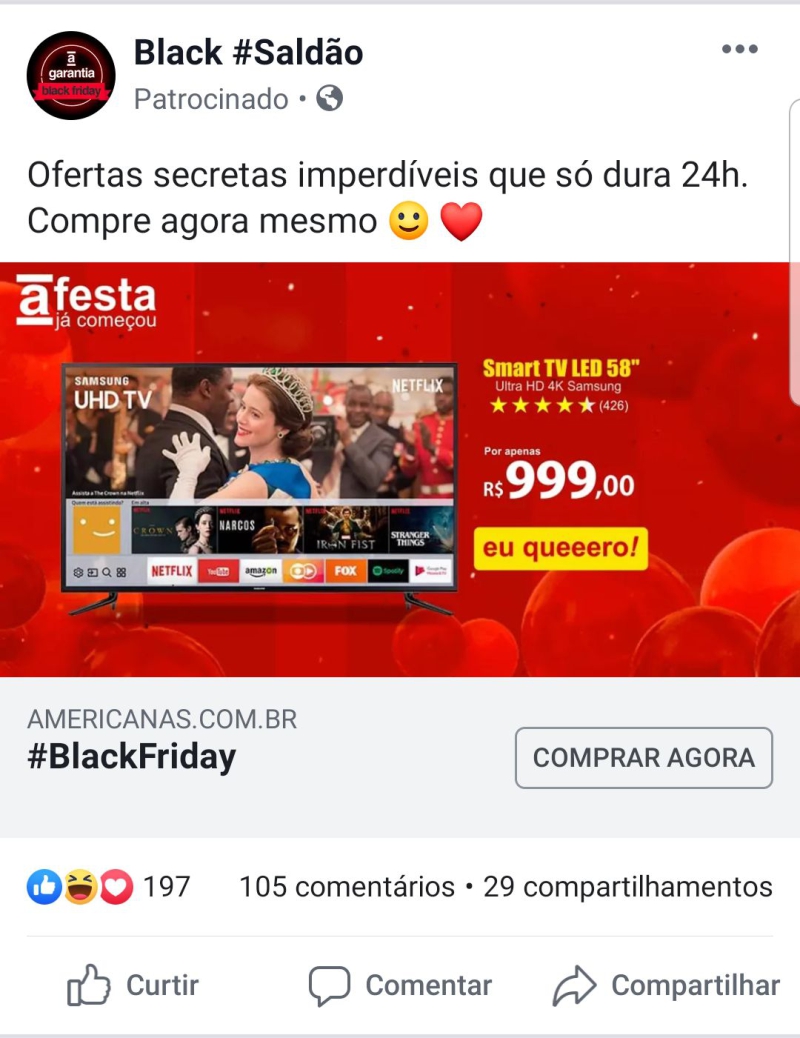
Having an internet blocking tool is essential to maintain security within the business and ensure that working time is used in the company's interests.
Lumiun Box : the best protection against Phishing
As we have seen throughout several articles here on Lumiun Blog, the main “key” to a Phishing attack are clicks on links to fake websites in various media, such as social networks, email and even SMS. To avoid Phishing problems, the best solution is certainly blocking websites considered harmful or outside the scope of work.
Imagine a simple, intuitive solution that does not require technical knowledge to be installed and that can manage the company's entire internet network without the need to install any type of software on the devices, blocking malicious websites, social networks, news, entertainment and a lot more. Well, this solution is called Lumiun Box . See some features and functionalities:
- firewall
- Blocking network ports, protecting company data and information
- Business VPN
- Control and protect remote connections to the company's internal data and systems
- Management reports
- Analysis of access in real time and for a personalized period, facilitating the creation of an internet access control policy
- Management of multiple networks
- Manage branches or networks from a single panel
With all these resources, the improvement in productivity when using the company's internet is evident, in addition to several other benefits:
- Prevents attacks on the company's network and systems , thanks to an extra layer of protection that helps block numerous types of viruses and malware;
- It allows information about access patterns to be consolidated and contribute to more assertive management, since managers will know which sites are most accessed, times, site categories, etc.;
- Contributes to the implementation of an internet access policy , with personalized rules based on the category of websites, security and reputation levels and schedules ;
- As it is cloud-based, there is no need to configure servers or special software;
- It has access rules applicable to all devices that are connected to the company's network, without the need for individual installation.
Count on technology to improve processes and remove daily concerns related to the company's productivity and internet security. Take a demonstration of Lumiun Box and see in practice how the solution improves internet use .
Until later!









