Ads on products and services are everywhere. When we are browsing social networks on our news site, emails, search sites.
We often see ads and do not even realize its content, perhaps because we are bombarded with such information.
In addition to privacy problems, ads can be a risk to security , considering that ad networks can be kidnapped, changing the destination that should be an offer or benefit to a malicious website or file. This attack is called Malvertising.
What is Malvertising?
The name is the combination of “malware” and “advertising”. Basically, hackers pay for ads on reliable websites that can:
- Mislead
- Forcing the malware download just viewing the ad
- Use visiting user features for cryptocurrency mining
There is no common place where ads can be displayed or an appearance that can be distinguished from a real ad. Pop-ups, banners, texts and even buttons may be infected with malware.
Later this year, New York Times and BBC website were advertising with malware, according to Knowbe4 .
The growth of the attack

The first occurrence of the attack occurred in late 2007, affecting sites like myspace through a vulnerability in Adobe Flash.
Already in 2011, Spotify, which was still an application only for computers, was hit by malware that affected users who did not have antivirus installed. The ad was a forced malware download and users didn't even have to click on the ad to be affected.
In 2017 the attack was even able to circumvent ad blockers, infecting the devices of users who used the lock tool exactly for this purpose.
reports of ads on YouTube with malware already emerged
In 2018 he was considered one of the main online threats, where some hackers modified the scripts already used earlier, absorbing so many features from the victim's computer that he could barely work.
In 2019, 1 in 250 ads was still malicious.
Some examples of real attacks
Below you will see images we collect here at Lumun and are still displayed daily with false offers of various products.
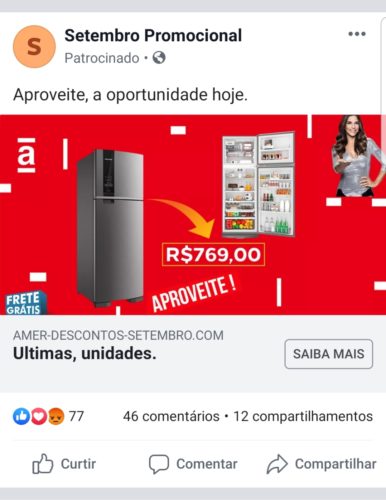
Note that the advertiser's name is “mega offers”, while the layout is from the American stores, well known on the internet. In addition, the price of the product is totally contrasting with the average prices of a product like this, and the destination link is “Vemcomprabaratoo.com” with an orthographic error. The evidence is many in this case.
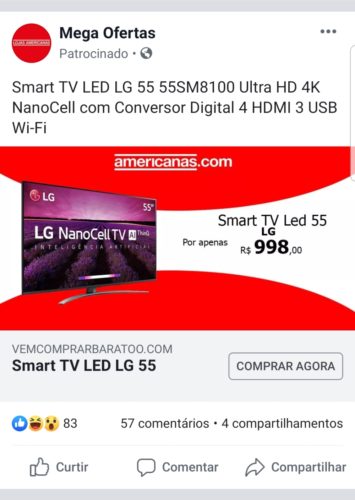
Another fake ad using the American Lojas website. Note that the name of the advertiser at the top is somewhat comic and unusual. Also, again the price of the product is not consistent with reality.
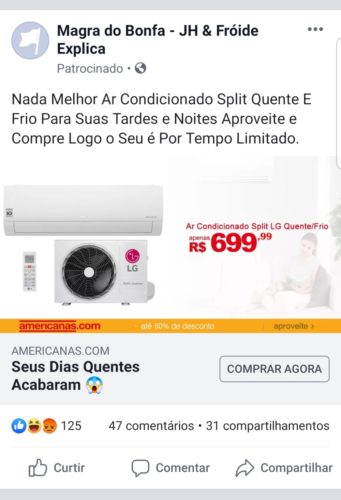
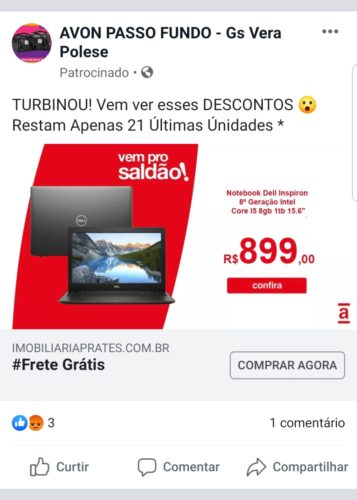
In another ad using the look of American stores, this attack is a little easier to identify. The first point is the name of the advertiser to the top, with an image not consistent with the company, and the name “Avon Passo Fundo” referring to another company, makes clear the blow. In addition to the price of the product, the destination site also shows “real estate estaters.com.br”, totally different from the area of activity of the advertised product.
Who wouldn't want a brand new, giant refrigerator with various functions paying a fraction of price normally sold? This is exactly why this blow has grown so much. As in the other examples above, the photo of the advertiser is generic, the name at the top is different from the ad, besides the price and link of destination are strange.
How to protect yourself?

There are several habits and tools to stay protected from malverting attacks. Constant improvements in large companies ad systems have improved content filtering that can be harmful to ad receivers. However, with each improvement, new shapes arise for hackers to introduce harmful material into ad channels.
With that in mind, we've listed some common practices that help maintain information security for professionals and businesses.
1 - Do not click on dubious links
Although reliable sites can be hit by this type of attack, sites that contain the largest number of dangerous ads are low -relevant sites.
Audits and detection systems of this type of attack are present on reliable sites known to most internet users.
Therefore, when accessing a dubious and low reliability site , avoid clicking on any link, especially ads. They may contain malware.
2 - Beware of the “gifts”
Donation and gifts are up to NGOs. Hackers just want you to click. Advertisements that promise free gifts or purchases should be avoided at all costs.
The main strategy in this case is to make the ad look as attractive as possible, and what becomes more attractive than easy and effortless money?
"Congratulations, you have been selected to earn an X free product." Do not click, as you have not been selected to earn anything, or rather have been selected to fall into the Malvertising blow.
Seeing an ad that seems too good to be true, remember that it is most likely not.
3 - What is the address of the links?
Over the years, large companies like Google and Facebook have done a good job requiring the site's viewing URL to correspond to the destination URL.
This avoids click fraud. If an ad can use the visualization URL you want, you can pretend to be Volkswagen by giving a free car, which are actually hackers trying to capture your data.
When you mouse over a link, and the URL viewing is hidden or not corresponding to the ad product or brand, you don't click.
4 - Advertising blockers
Advertising blockers do not protect from all malverting schemes and will certainly not protect you from malicious sites in general, but it is still a good layer of protection if you follow the previous tips.
As I said earlier, new strategies to circumvent ad blockers are created daily, implementing a digital arms race for protection and attack all the time.
5 - Web content filter
Perhaps the most effective solution for Malvertising attacks is the DNS content filter . DNS filtering can evaluate site content rating and lock before any malware can settle on the user's device.
In addition, blocking websites considered harmful, can protect the user against general cyber attacks such as phishing and data kidnapping.
The best layer of protection for companies is one that does not depend on the knowledge and goodwill of users, and for this, only site access blocking can do.
Lumiun is a Brazilian internet access control tool, with local currency payment (R $) and with fully Portuguese support . Specializing in information security improvements for companies and professional productivity, Lumiun has features such as firewall , web content filter and business VPN for safe remote access.
You can see more details in our presentation , available for free download.
To finish
Concluding this article, it is important to emphasize that the vast majority of social engineering attacks in companies occur due to lack of knowledge and over consumption of content outside the scope of work, impairing the security of the company's data and also the productivity of the team.
Our goal here at Lumun is to help companies identify their needs in this regard, and implement systems and processes that meet the general objective of the organization.
To the next!












3 Comments
Comments closed