Awareness is the first and most important step to start the malware protection process. The problems caused by viruses and malware have no right date to happen, and for this reason, it is very important to know how these threats work , what damage they can cause to devices and machines and how to combat intelligently.
Infections caused by malware can arise subtly without even if the user realizes that he is facing a fraud or a threat. Knowing what are the cyber threats and how they behave, it helps to establish an efficient defense process that will help keep your devices always protected. Being prepared to ensure the digital security of your business can make all the difference.
Although many believe that malware refers to a specific type of cyber threat, it is important to remember that it consists of a large term that is used in classifying various types of malicious software. These programs are always used to cause damage or damage , either due to damage to the system and devices, information theft, financial fraud, among many others.
To help you establish the best strategy, we set up this complete material about everything you need to know about this threat and thus be able to find out how best to defend yourself . Let's go?
What is malware?
Malware is a term derived from the English language that was built from the junction of two terms: malicious , which means malicious in English, and software , which refers to applications and programs . Thus, we can understand malware as any program or cyber resource created to cause some kind of damage to devices or damage to users.
Based on this, we can define malware as a broad classification used to refer to other more specific and directed threats such as viruses, ransomware, spyware and many others.
The main objective of malware is to cause problems or apply scams, which can be:
- Improper collection of personal data for financial fraud;
- Identity theft;
- Credit card information theft , such as number, passwords and security codes;
- Manipulate and control devices remotely to favor other cyber threats , such as DDOS attack;
- Turn devices into botnets (infected computers that can be remotely controlled) for bitcoin mining and other cryptocurrencies;
- And many others.
Types of malware
Since malware is a generic term used to refer to a set of cyber threats, it is important that we understand the characteristics of each of them:
Virus
This type of file is usually attached to false or malicious emails, usually disguised from a reliable sender or legitimate company. When the user downloads the annex or opens the suspicious link, the device ends up infected.
And this malicious software can lead to numerous problems, depending only on the intention of the cybercriminal, such as interrupting the use of certain important applications and functions, causing slowness, preventing the device to function and many others.
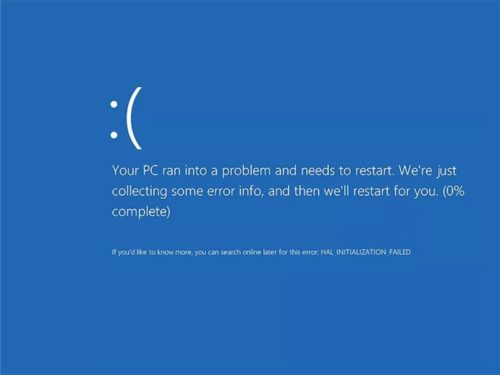
Ransomware
Ransomware and profitable cyber threat to the cybercriminal. This type of malware, once installed on the user's device and allowing misconduct to information, is encryption of your files . As a result, the user can no longer access this data and is vulnerable to the criminal's threats and demand.
From there, the criminal charges a redemption amount so that access is restored and information is not harmed or worse: leaked on the Internet.
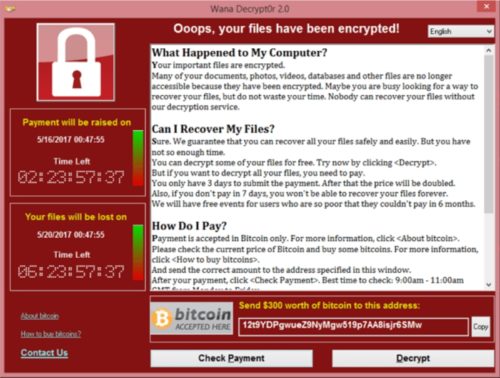
Scareware
Through this scam, the cybercriminal causes his victim to think that he is under a threat or in the face of a virus infection. To do this, it sends alarmist content so that this user downloads software or application that can supposedly help get rid of this problem.
This type of scam can come in many ways: whether by an email, spam, pop-up, suspicious sites banner , and many others. Scareware usually provides phrases like: "Your computer is infected," "your device is in danger," "it has been identified that your computer has x virus," etc.
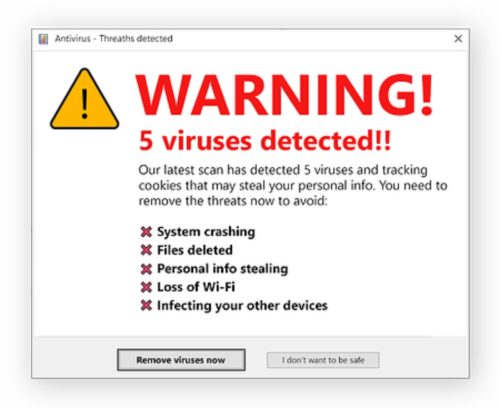
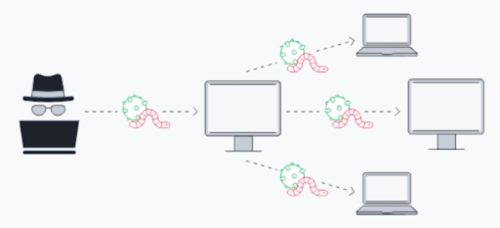
Worms
This threat is quite dangerous, especially for companies. This type of malware has the ability to spread from one device to another through safety vulnerabilities.
There is no need for user interaction to work and can infect thousands of positives in a short time. With this, he can contaminate all computers in a company and cause numerous damage to the business .
Spyware
This type of malware has gained a lot of visibility in recent years because of its wide use by government and security to support investigations and monitor communications.
However, this application is also used for malicious purposes. Through the software, cybercriminals can access devices and capture personal information , message applications, confidential data and more.
For companies, this type of improper access can cause major problems. This information can be used for ransomware blows, passed on to competition and even leaked on the internet.
Understand how this type of malware works in the video below:
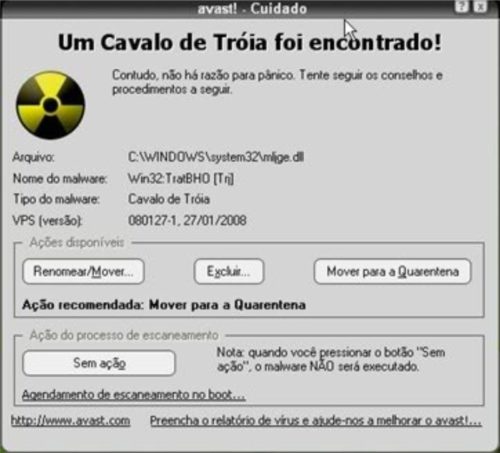
Trojan Horse - Trojan
This is one of the best known threats on the internet and was long most used in the digital environment. Disguised of safe and harmless applications, Trojan horses are installed on the devices, and can steal confidential information, damage the proper functioning of the machine, spy on activities or other threat.
In fact, the Trojan horse acts as a means of disguising cyber threats , facilitating devices contamination and creating vulnerability points.
Adware
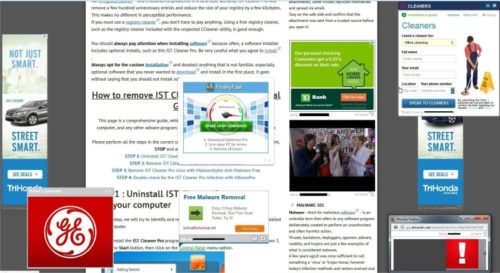
Although it does not seem like a very large threat, adware attacks send numerous unwanted ads to users , with windows or flashing or pop-ups when a certain action is performed. These programs are installed without user consent and can cause a great discomfort.
In addition to damaging the devices properly functioning, Adwares can serve as a disguise for viruses and other malicious programs , which are installed when an ad click.
How can malware harm your business?
As we have seen, software that are part of the malware set can be used in many ways, each with its own purpose. Among the main problems they can cause, we can mention :
Confidential information theft
This type of leakage can harm companies from various sectors, especially those dealing with storage of personal information from users, customers or suppliers. Cybercriminals collect this data and may apply for redemption payment (ransomware) , leak information from the internet or sell to other criminals or companies for malicious purposes.
Personal data, confidential information, financial data (credit card numbers and passwords), customer profiles, navigation historical, access passwords, and more. Do you know the risks of data leakage for your business? Access this article and find out!
Impairs device performance
Once malware is installed, the device may have an inappropriate functioning, such as slow, locking and unexpected behaviors . In addition to being extremely uncomfortable, these problems can disrupt the routine of work, cause delays and increase the incidence of errors.
Infected devices can have important functions compromised, and even suffer from data loss and valuable applications for continuity of activities performed.
Loss of access
Some types of malware, such as ransomware, can prevent access to important information that is used by the company. In this sense, it is essential to have a backup tool that helps maintain a security copy of all stored data.
Although the threat represents a huge financial risk, the company can still rely on a copy of all data, and may maintain the continuity of services.
In addition to these problems, malware can also install additional computer software on the computer , display several unwanted pop-ups, change device settings, redirect research, cause full interruption of services, and many other problems.
Viruses and Malware: Are they the same?
Now that we understand what malware consists of, it is much easier to understand how it differs from viruses. As we have seen earlier, malware can refer to any kind of dangerous software or application that causes some damage to computers and other devices.
Based on this, we can understand the virus as a variation of malware and can replicate and spread automatically. Using a simple analogy, we can conclude that every virus is malware, but not all malware is a virus.
This is because malware consists of only one category of cyber threat , and the virus represents a direct threat, as is the Trojan, Spyware and Ransomware horse. Understand the difference between these threats through this article .
Tips for protecting yourself
Malware can reach in many ways to the victims and cause numerous damage according to their type and objective. For this reason, it is important for the company to establish a security protocol that helps identify and combat these threats, for example:
Beware of downloads
Many malicious applications arrive through disguised emails and false internet pages. For this reason, it is important to be very careful with any type of file that is downloaded on your device, whether received by email or on the website of a company considered reliable.
Many cybercriminals send this type of malicious software through supposed free materials, fake slips, attachments in phishing emails , suspicious links, etc.
Everything installed on your device should be carefully monitored and analyzed by a security application .
Escape from unwanted emails
Phishing is a threat that can be directed to any type of user, reaching from the most lay to the most experienced . Who has never received a fake email, even if it is from a company that you believe is legitimate? Or an alleged message that was sent from a known recipient?
This type of content is very dangerous and can cause major problems for users and businesses, so it is essential to pay attention to this threat. Do not open suspicious attachments or click Links without a prior security check. Unmissable promotions, free courses, awards, unquited files… All this can be very dangerous for you and your information.
Avoid certain contents
There are pages on the internet that specialize in hiding cyber threats such as pornography pages, sensational content sites, and others. These sites are widely used for the dissemination of malware and access to this type of content should be carefully monitored.
In this sense, the company can count on a user access program or access control system that helps monitor and block certain content types and keep your network more protected. Check out this guide to access access to malicious websites we make available on our site.
Count on protective tools
Counting on protective tools such as firewall, antivirus and other features is an extremely important factor for those who want to keep their devices always protected and safer.
Although it seems an obvious tip, there are still several users and companies that end up underestimating the importance of this type of tool , and consequently favor the creation of vulnerability points that increase the likelihood of suffering from cyber blows and threats such as malware.
In addition to choosing a tool that meets your business demand, it is important that it is always up to date to prevent further threats from reaching your devices.
Create an internet use policy
It is also very important to establish a awareness protocol with the entire team involved in the company's processes . The more employees are prepared to understand how major cyber threats work and how important it is to ensure safe behavior about the digital environment, the easier to ensure more security for information.
For this, managers can develop a conscious use policy of the internet that will help compile all rules and rules of conduct focused on digital security. Check out this guide we have prepared to help you!
Lumiun Box: Block the company's Internet websites
Often, even with an internet use policy, some employees may have insecure behavior in the virtual environment. To avoid this type of problem, you can have a monitoring and control tool for the use of the internet, such as Lumiun Box .
With his help, managers can implement custom access rules and can help maintain safe use of the company's internet and increase the security of information that is stored.
Blocking certain resources and content can help reduce exposure to the main cyber threats present today , avoiding risk behaviors and reducing the vulnerability of the company's devices and networks.
Make a and free demonstration request a free test and see how the solution can help you.
Until later!









