Outside a specific context, the word "report" reminds us of something that few people like to analyze and that fewer people still like to create. But this scenario, contextualized in a corporate environment that needs an analysis of internet access, is very sought after, especially by managers and IT professionals.
On the one hand, technology professionals seek a way to generate statistics and numbers visible to their managers in an attempt to “prove” that waste of time and malware infections on the company's computers come from accesses that should not be released. On the other hand, managers want to be aware of the use of the company's internet and try to identify problems with waste time on the internet, using access reports.
In this article, you will see why companies should get and analyze internet access reports and also know a simple and easy way to get this information.
Reasons for obtaining internet access reports
The reasons why companies are looking for tools that offer internet access reports are numerous. Most, it is linked to the desire to obtain more productivity and security on the company's internet. But beyond that, there are other reasons, which you will see in the next lines.
Slowness in the company's network
Improper accesses and malware -infected computers, degrade network performance and may delay or even make it impossible for many or all employees who use the company's network in their daily lives.
Companies with slowness problems in the network are looking for reports to identify which or which equipment are consuming the entire internet band, for example.
Lack of focus and waste of time on the internet
In environments where the internet is widely used to perform work tasks, it is common to use for other purposes, such as access to social networks , messaging apps, videos, music, news among many others.
Given this, it is natural for IT managers and professionals to look for access reports to identify which sites outside the scope of work are being accessed and then blocking them in some way.
Excessive cost with equipment maintenance
We know that not all companies have one or more responsible for the company's technology industry. These usually hire third parties for maintenance when necessary in order to reduce costs. However, when the use of the internet is done inappropriately, equipment maintenance costs may be higher than having a full -time professional within the company.
In addition, infected computers cause damage to the systems used by the company to perform their daily work, as well as leaving company data vulnerable to cyber attacks, which may cause high maintenance costs in the event of malware, or to block the operation indefinitely in cases of cyber attack.
BENEFITS OF ACCESS REPORTS
Imagine that you can quickly see the entire internet use scenario and realize several aspects that were once "in the dark." What information would you like to know first?
Well, many would not know very well what to answer, but the benefits and possibilities are many, and perhaps you can find out how to answer this question more easily after reading the text below.
Perception of team time waste on the internet
With the implementation of a management and control solution of internet access to the company, it is possible to view important information in the access reports.
Perhaps one of the most sought after by small and medium -sized managers is the report of which sites are being accessed. Thus, it is possible to identify possible causes of waste of working time on the Internet.
Facebook, Instagram, Tiktok, YouTube, among many others, may be consuming the team's attention and focus on the internet during work.
Access reports may facilitate the decision of which sites should be filtered and which employees or group of employees will receive different access rules from others, benefiting the productivity of the team in general, without sacrificing the productivity of those who need specific access.
Identify infected equipment with malware
Complete tools for the company's internet management are able to offer access to websites considered harmful, even separately by equipment. Thus, the professional responsible for identifying problems with virus and malware infection, has his task shortened, and can correct the problem before it becomes something more serious.
Also, when identified which equipment is doing this type of access, and then the proper steps are taken, the company's data and systems protected from cyber attacks and breaches in the company's internet security are maintained.
Improvement in the company's network performance
As we mentioned earlier, unlimited internet access to the workplace can bring various headaches.
Malware can use the Internet from the infected equipment to mine digital currencies, corrupt files and systems and compromise the general performance of the company's network.
Having a network performance report by equipment makes it easy to identify which equipment is infected and makes the network healthy and available for work tasks.
How can I obtain reports on the company's internet access?
In smaller scenarios, with few equipment, access reports can be done manually or using simpler and more free solutions. However, in business environments with various devices, users and sectors, the management and control solutions of internet access are more appropriate, as they bring reports automatically, customizable and specific to business use.
Among the most common are Cisco Umbrella (OpenDNS), Lumiun Box , DNS Filter , Fortinet FortiGate , pfSense and the use of Proxy on a Linux server. However, the solutions differ greatly from each other, and do not always adapt to all the diversities found in the business environment.
Interface, technical support, reports and functionalities are decisive factors when choosing a tool for managing internet access in companies.
Lumiun Box, however, is a Brazilian solution, aimed at small and medium -sized companies, with characteristics and features focused exclusively on this audience, and with local currency payment.
This way, in the next lines you will see the reports generated by the Lumun solution and the main features of each.
Lumiun DNS reports
Lumiun DNS offers a comprehensive set of reports that allow you to monitor and analyze the use of the internet on your network, helping with access and access control. These reports are accessible through the control panel in the “Reports” section, and are divided into three main categories:
- Statistics: In this section, you get an overview of internet use, including:
- Requests Volume: Graphs that show the number of requests released and blocked over time.
- Most accessed domains: List of the most visited sites by users.
- More blocked domains: Identification of sites that had more blocked access attempts.
- Most active filters: Information on which filters or applications is blocking the most accesses.
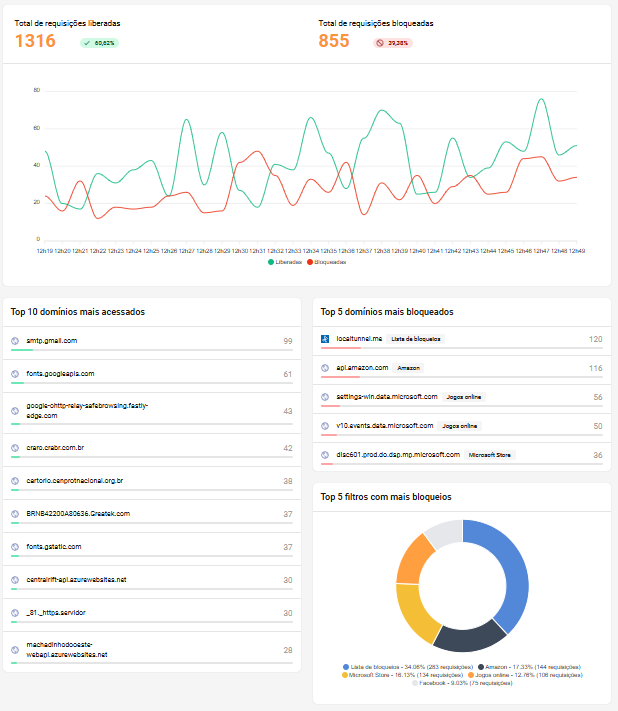
These statistics allow us to identify patterns of use and possible threats to network safety.
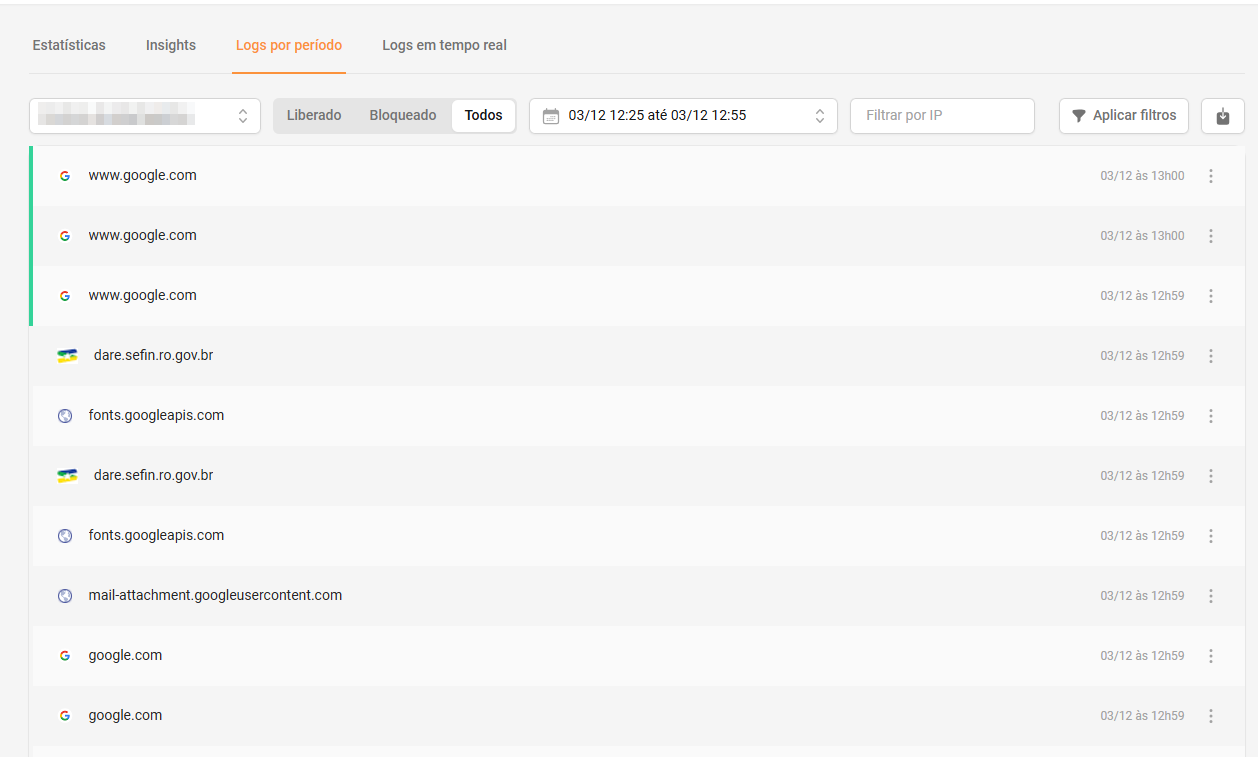
2. Records per period: Here, it is possible to generate detailed reports for specific periods, up to 7 days within a 60 -day interval. These records can be exported in CSV format, facilitating the analysis and sharing of information.
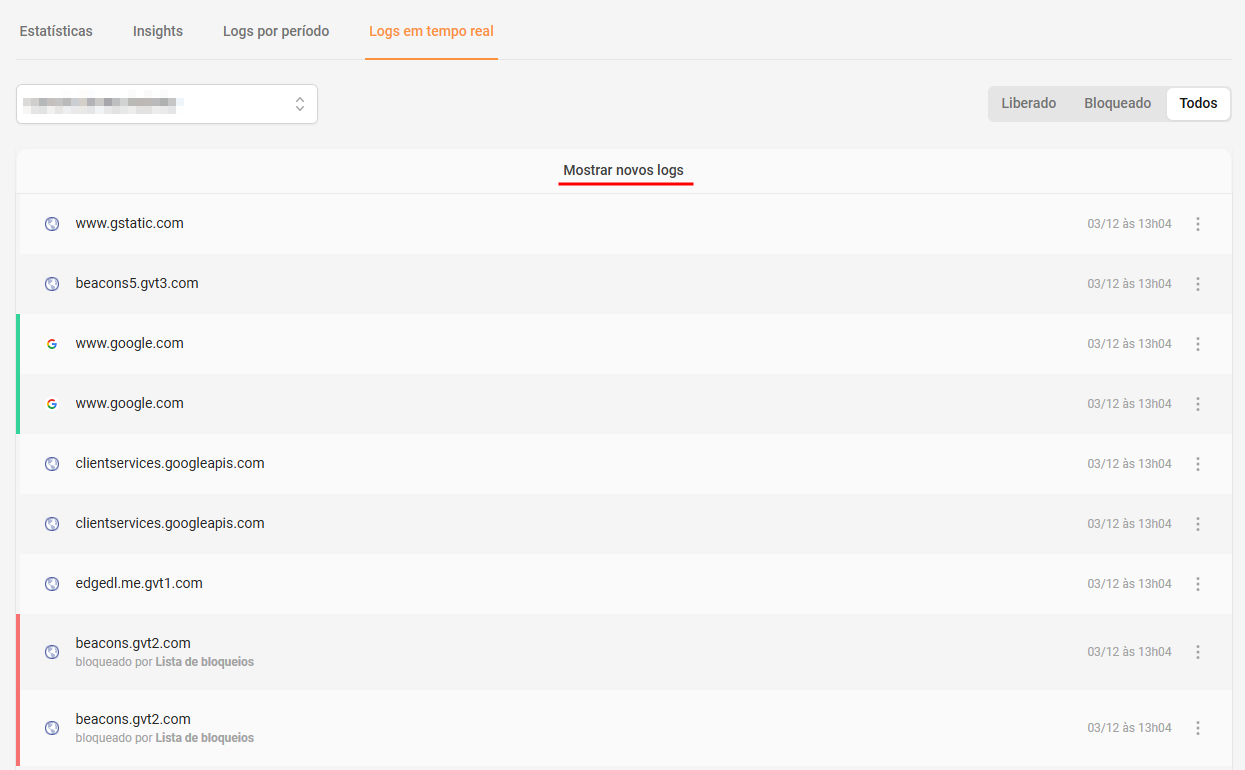
3. Real -time logs: This functionality allows you to track, in real time, DNS requisitions made on the network. It is useful for identifying unwanted access or unexpected blocks, enabling immediate actions.
In addition to these features, Lumiun DNS offers:
- Data Export: Possibility to export reports in PDF or CSV formats for external analysis or presentations.
- Personalized filters: Application of filters by location, period and type of request (released or locked) for a more accurate analysis.
- Identification of internal devices: When configuring correctly, it is possible to identify the internal IP addresses of the devices that made each request, providing greater control and safety.
These features make Lumiun DNS an effective tool for monitoring and managing internet use in corporate environments, contributing to network safety and productivity.
Lumiun Box reports
Lumiun Lumiun Box has a report module that helps save time and find information that can be useful for network security and employee productivity.
Within the Lumiun Boxreport module, many can be viewed and many of them can be customized as your need. See below some.
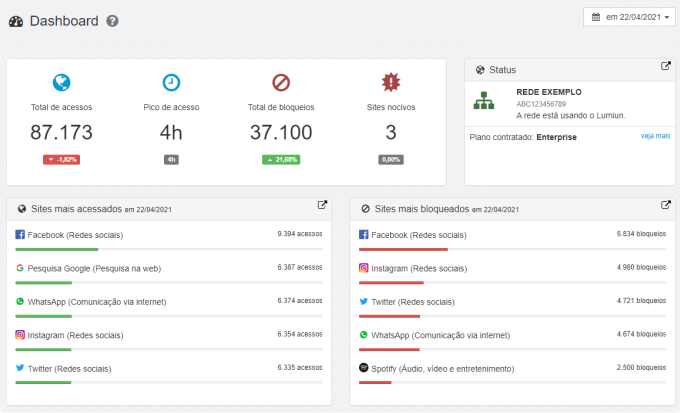
Dashboard
On the first page of the Lumiun Box control panel the first report can now be viewed. These are statistical data that demonstrates a summary of the previous day's accesses such as the amount of access and locks, time with the access peak, blocked harmful sites, more accessed and locked sites.
Real-time access
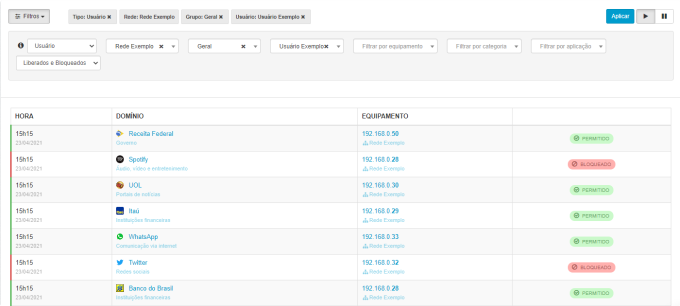
With Lumiun Box it is possible to track in real time the Internet accesses of all network devices and users.
Through a table that is automatically updated, access requests are displayed by identifying the time, website, equipment, user and whether the request has been released or blocked.
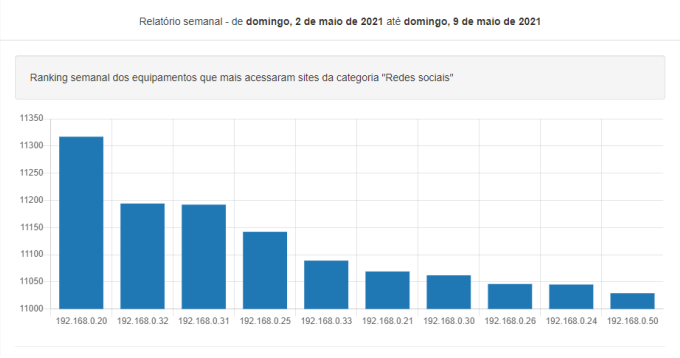
Devices that most access social networks
In the Lumiun Boxpanel, you can view the device report that most access social networks in a given period.
More blocked websites
In the report, you can view which were the most blocked sites in the specific period.
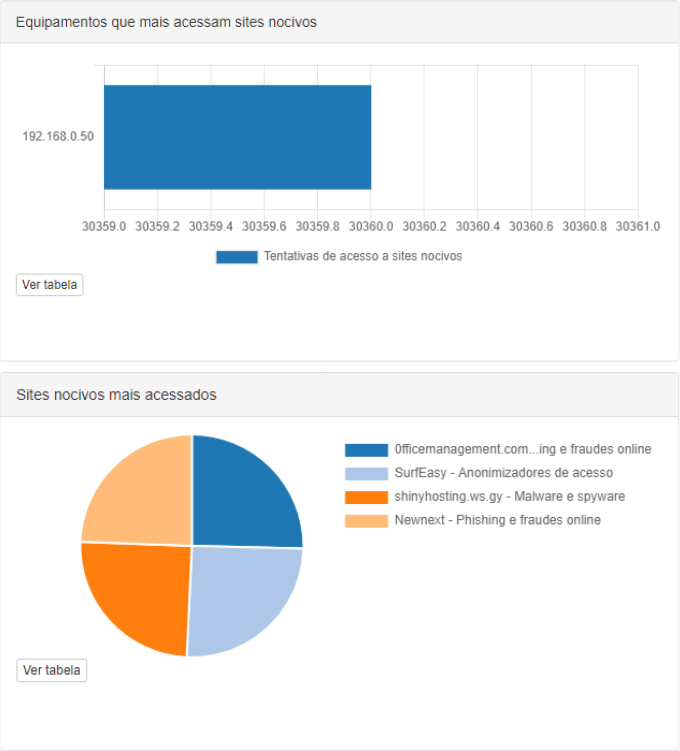
Equipment that most requests for harmful websites
In bar -shaped, this security report shows which equipment is most attempted to access harmful websites. Thus, it is possible to quickly identify equipment that may be infected.
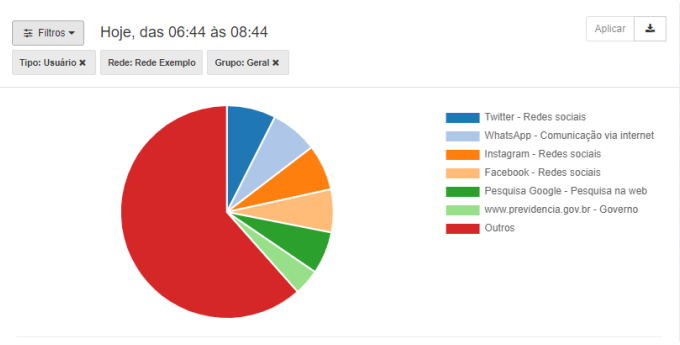
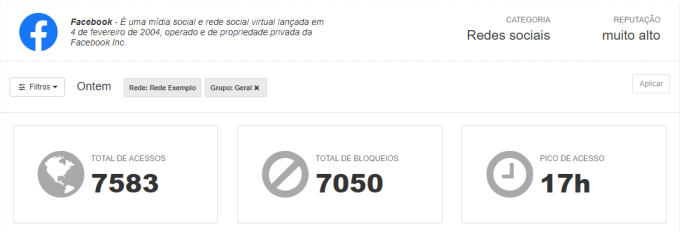
APPLICATION ACCESS REPORT
In this report you can get information about a particular application. In the case below, Facebook is visible the total hits, total blockages, peak access time, most accessing equipment and more.
If you suspect that a specific application is hindering the focus of the team, in this report you can easily answer your questions.
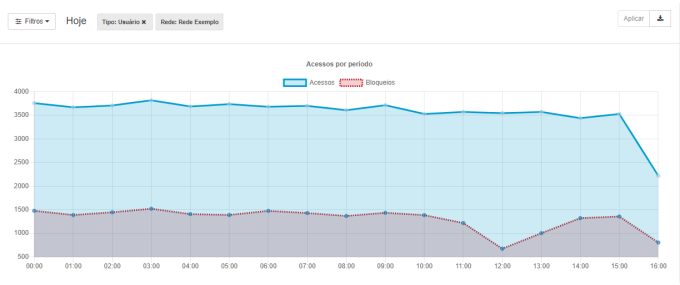
Accesses by period
This report displays in a line chart the behavior of access requests in a given period. It is widely used to define and metrify blocking and release schedules for internet access to the company, identifying which periods are the most idle and the use of the company's internet use.
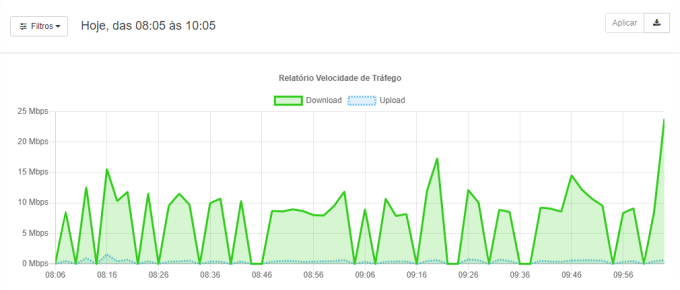
Traffic speed
In this, the average download and upload speed of the company's internet is displayed in a specific time track. Thus, it is simple to check at which times the internet is being most used and if this is interfering with the performance of tasks.
If there is a peak of consumption, you can click on a specific point of the chart and see in detail which equipment that resulted in this increase. This makes it easy to apply a download or upload limit rule for certain equipment groups.
Internet access control guide to companies
Throughout the article you have been able to realize the importance of obtaining relevant information in internet access reports in the company. However, for the reports to be generated, you need to use an internet access control tool. With that in mind, we create the Internet Access Control Guide to companies , which you can access freely when you want, or download and send it to your colleagues and friends.
The guide tells some topics such as:
- Why control internet access in the company?
- Some solutions
- 5 steps to fully manage internet access
- Use cases
- Internet access control for remote employees
- Controlling internet access from multiple networks in a single panel
- Success stories
- Free Materials
We hope the Internet Access Control Guide to companies can help you in some way.
The internet is an extremely useful source of information and work tool for companies, but almost everything, it has its cons. Balancing the use of the internet in the business environment is important and should be part of the daily life of companies.
I believe that if you were looking for information on the company's internet access reports, you were able to identify various possibilities after this reading.
Until later!











1 comment
Comments closed