E-mail is one of the most important tools today, being present in activities within the corporate and business routine. There are several activities that require the use of this tool, and for this reason, ensuring a safe email becomes a priority for companies and their employees.
The biggest problem in using email is that although it is extremely functional, it is not very safe . According to the ESET Security Report 2022 survey, there was only a 226% increase in phishing attacks , which uses email as the main tool.
To help solve this, there are some essential care that helps bring more protection to the exchange of information and your resources.
Its lack of security is due to the various intermediate channels that messages go through, such as email providers and customers until it reaches the end user. But the main security problem of emails is directly related to user behavior .
Because it is a tool with a low safety standard, email has been used as a gateway to various threats.
How to leave your email safe?
Di before these problems, you must be wondering: What is the best way to make email safe?
There are several people and users who are malicious in the cyber environment, making protective tools much more than just one detail: they are essential to ensure more privacy and security for this messaging tool.
One of the most common and also very “successful” phishing attack uses email as its main resource for scam application, malware spread, viruses and spam , and many other traps that can undermine information security.
Using social engineering, these criminals can fool users and make them provide confidential information that favor the application of scams and impair the security of the company. Understand better how this strategy works in the video below:
Main threats that arrive via email
As we have seen, the email can be the gateway to several blows and threats, impairing the continuity of the business, the safety of information and the financial health of a company . Here are some of the most common threats that can be deployed through this tool:
Spam
Spam old problem in the digital environment. We have all been massacred at least once with this type of message, which besides being extremely uncomfortable, can mask some dangerous trap or strategy for the business.
Usually used for advertising purposes, spam can make the inbox full of unreserved and unnecessary emails, and can also be a channel to favor cyber attacks.
For this reason, it is very important that there is a lot of caution when opening emails from unknown senders or with false promotions, too good to be true.
Phishing
As we said earlier, Phishing is one of the main traps that can arrive by email . Unlike spam, phishing not only uses the advertising proposal to reach users. This strategy can come in the form of false collection messages, emails from known recipients who have been hacked, among other farces, and the main objective is to induce the user to provide confidential information .
These data collected in a criminal manner may not only impair your safety, but also contribute to the application of financial blows.
Malware
Malware refers to applications or software that can undermine the safety of a company's devices and networks. In this sense, malware is considered applications that can lead to some kind of problem for information, such as viruses, trojan, spyware , among others.
These applications are used according to the purpose of the cybercriminal, either to steal access data, credit card information, corrupt valuable data, prevent users access, among others.
Social engineering
This strategy, as we mentioned earlier , is used by cybercriminals to deceive and deceive their victim , being widely applied to phishing blows. Through it, criminals can efficiently disguise their intentions, and make users make confidential information available.
Social engineering can be a great danger to users, from the most lay to the most experienced.
How to keep your email safe
Now that we understand how email can be used to deploy threats and favor various types of scam, we need to find a solution that helps make the tool safer for all users .
To help you, we have separated some essential tips that can make your email a safer and reliable tool to use within the corporate environment:
Stronger passwords
Although it is a care that is quite frequently publicized, there are still many users who use very simple or easily guessed passwords on their email tools.
Another very much made mistake is the use of a single password to access various applications or services , thus facilitating the work of the cybercriminal. It is very important that there is an orientation to stronger and more complex passwords .
For this, a combination of numbers, special characters and uppercase and lowercase letters can be used to make it difficult to guess and make your email safer.
We have a complete guide for the creation and management of more securely . Click here and download for free!
Authentication of two factors
Depending on your provider or email service, it is possible to insert authentication of two factors, which is nothing more than an extra layer of security for login and services.
For this you can use a mobile number, a USB device, token or another tool, depending on the email service used. With the help of this extra entry code, the user can leave the email safe and prevent it from being easily invaded by cybercriminals.
Encryption
Information encryption is a resource that helps keep the email safer and ensure the privacy of information. Depending on the email service, encryption is already embedded, as is the case with Gmail , which is Google's email.
However, in this case, the encryption service only works when using Google apps or your browser, Chrome . Another detail is that both users must be Gmail users so that encryption works. In any case, it is essential to verify that your email service supports this functionality.
Tools for blocking viruses and malware
Through the phishing blow, cybercriminals can send corrupted or contaminated virus and malware files that cause major problems for the company. Antivirus software for email helps block the main threats present in the online environment, including those that are received through corrupted links and attachments.
Relying on a lock tool helps to prevent these threats from being installed on the device and causing problems for the user.
It is equally important to ensure that these tools are always up to date so that they are prepared to deal with threats as they evolve.
Avoid opening annexes
As we see, many of the threats that arrive through email are present in the attachments of these messages . Due to this factor, it is important for employees to understand the importance of paying attention to the referrals and attachments received.
Blocking automatic download of these attachments is a smart strategy that helps to increase safety and ensure a safe email. As reliable as this file may seem to be, it is important that it is verified by a scanning service before it is effectively opened by the user.
One way to avoid the blows received through attachments is by implementing a cloud service in the company . This way, employees will exchange information through this service and no longer through attachments.
Security checklist for email
The tips we brought in this article can help increase the safety of your email and avoid the incidence of various cyber scams. To help you, we have also prepared a security checklist for you to check your email step by step and the main strategies that should be adopted to add even more protection.
- Check reliability of your password.
- The internet is full of tips for having a safe password
- Ensure that each email account is used a and secure password
- Activate authentication of two factors ;
- Use an antivirus and ensure that it is updated as needed;
- Perform the update of the browsers used;
- Do not open links to emails of referrals that are not known or reliable;
- Block automatic attachment download;
- Ensure strong passwords for home office connections;
- Avoid public networks as they are a higher risk of safety.
Is failing to protect the email a risk?
As we have seen throughout this article, there are several threats that can arrive through email and can cause numerous problems for the company. Failing to protect your email can be a great risk to both users and business.
The leakage of information, for example, is one of the problems that has been causing many damage to companies, causing penalties and impairing their image in the market.
It is very important that employees understand the importance of using a safe email in the exchange of daily information. To help, the company can establish an awareness policy that helps employees understand the importance of digital security for all.
You can also implement a security checklist, such as this model we have made available on our site , so that all users check the characteristics and practices that should be implemented for a safe email, and ensure more security for everyone.
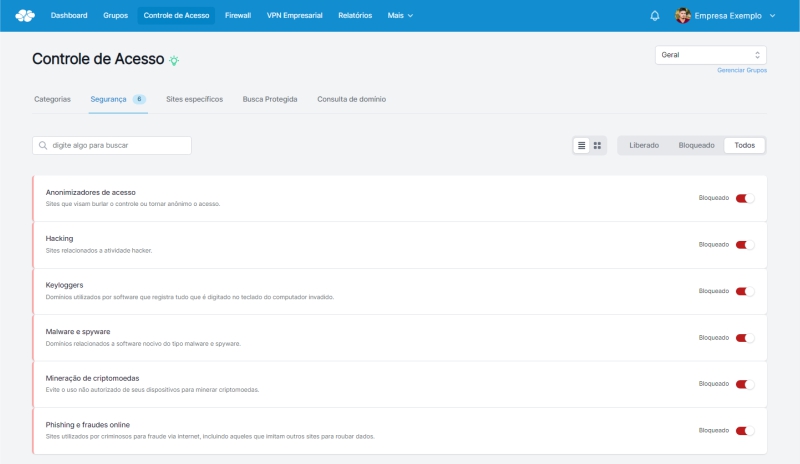
Blocking threats with Lumiun Box
With so many threats present in one of the largest business communication channels, email, the task of “taking care” if the email, link, sender or file we are receiving is really safe and reliable source . The Lumiun Box was created exactly for this purpose. Make access to the internet, websites, links and files, especially from companies, safer and more quiet, eliminating managers' concern and also improving the productivity of employees on the internet.
In short, Lumiun Box Block sites categorized as harmful , with inappropriate or administrator's choice, such as social networks for example. With several categories available, it is possible to customize blockages and separate user groups . The financial sector for example can receive blockages from social networks and potentially dangerous websites, while the company's marketing sector has free access to social networks but has the extra layer of protection.
This way, links, files and access to websites that can bring dangers to company data and information , either in email or any other internet access channel, will be blocked effectively.
In addition to the blockages, Lumiu Box has several other features, see:
- Business Firewall
- Extra protection with door lock
- VPN Business
- Safe and controlled remote access
- Traffic Management
- Control the accesses in a single panel
- Management reports
- See personalized internet access reports and also in real time
Want to reduce your concerns about the company's internet security? Make a quote without commitment and see in practice the benefits of Lumiun Box .
Until later!