Coming in the form of unmissable promotions, miracle medicines, crazy ways to make money and thousands of other misleading promises, spam can arrive in different ways and with different temptations. You've certainly already received content like this.
Spam is a strategy implemented by companies that seek to promote their products and services cheaply and reach as many people as possible. Although it has been practiced since the beginning of the internet, this strategy is not well regarded by users and the market, especially after the arrival of the General Data Protection Law .
This is because this legislation's main objective is to make companies collect data and send information to their consumers only with their respective consent. In the case of Spam, consent is non-existent.
In addition to being subject to the penalties imposed by the LGPD , the company that ends up known for sending Spam also ends up having its image damaged in the market and being frowned upon by consumers, after all, it is an uncomfortable and unnecessary type of content.
Put simply, Spam consists of an electronic message that was received without the recipient's request , usually with advertising content. But do you know how this type of content can pose a risk to you and your company? To clarify all your doubts about spam, we have prepared this complete material with everything you need to know!
The origin of Spam and some examples
Spam is a practice that has been implemented for many years to send advertising content. Although we are used to hearing this term and using it in our daily lives, many people still don't know its real origin.
The practice of sending unsolicited messages through electronic channels was named Spam after a comedy sketch by the British group Monty Python . In one episode in particular, two consumers are in a cafe and notice that a canned product from the North American brand SPAM is present in all items on the menu, causing it to be consumed regardless of the customer's wishes. Watch the full episode below:
Because of this, the practice of sending unsolicited content ended up being called Spam. The main characteristic of this practice is the mass sending of propaganda to random recipients . With this, the spammer (who is the person responsible for sending spam) seeks to reach as many potential consumers as possible so that a small portion is returned.
By analogy, we can understand the practice in Spam as fishing with a net. A large net is cast into a lake so that the greatest number of fish can be caught with this strategy. By concept, this strategy is very similar to the practice of Phishing , however, its objective is to obtain consumers and customers.
Although it may seem interesting for a company to carry out a low-cost marketing strategy, these messages end up having a huge impact on the business image . This is because they bother many users, who, in addition to blocking the content, may also report the message as spam.
Thinking about the impact this strategy can have within a company, productivity problems certainly top the list. Workers end up wasting time with messages that are not in the company's interest and putting the business's strategy and digital security at risk.
Another very big problem caused by this type of unwanted content is the loss of important tasks . In a sea of unnecessary emails, important content for the company may end up going unnoticed, hindering the continuity of tasks, causing delays and impacting the company's image in the market.
Email is one of the most important communication channels in the company-employee relationship, so it is essential to ensure that this is a space free from distractions and content unrelated to the needs of the business itself, ensuring online productivity .
Some email providers, to combat threats, started tracking the IP of the server where these spam emails came from and created a blacklist of senders. When a company ends up on this Black List, all its emails are automatically classified as spam , greatly damaging its image in the market.
In addition to email marketing spam, which is the most common form of this type of unwanted content, users can also receive misleading advertising spam.
Consisting of a strategy of false offers and promises, this type of spam aims to make the user open a malicious page or website and provide their confidential information. These emails can come disguised as irresistible promises, such as miracles in the form of weight loss pills, products to make hair grow, among other strategies.
The danger of unwanted emails
As we have seen, there are different types of spam that can not only cause inconvenience, but also security problems for your company. Although most spam emails aim to deliver commercial strategies, this type of content can also harm your company's digital security.
To implement the strategy, companies end up obtaining users' email data without consent, generally through lists and companies that sell this type of information . Some of these spam emails may contain corrupted files that can contaminate company devices and networks.
These points of vulnerability favor cyber attacks and other threats that can cause substantial problems for the company, such as financial losses, loss of information, data leaks , among other situations.
Furthermore, in addition to security problems, the company may also suffer from the loss of employee productivity. When received in excess, this type of content ends up distracting employees and hindering the execution of activities that are truly relevant to the business.
Spam and Phishing, what's the difference?
As we have seen, Spam is the term we use to refer to emails (with advertising, chain letters or misleading advertisements) that were unsolicited and are sent in bulk. To differentiate it from phishing, we need to clarify some essential characteristics that help differentiate one strategy from another, such as:
Spam
Spam typically contains a commercial message, seeking to offer services or products. In general, this type of email has the sole objective of delivering a commercial strategy . In some cases, the email may contain a link to the company's website or the product/service being offered.
This type of content may also be related to the user's browsing data, such as searches carried out on price comparison websites and stores, and registrations made.
Phishing
Phishing is a fraud attempt through which cybercriminals seek to obtain personal information or financial data from their victim. To do this, he uses tools and social engineering . This type of email is a malicious strategy, whose objective is to collect personal data, carry out financial scams or promote cyber attacks.
This type of email, unlike spam, contains malicious links to fake websites or corrupted files, aiming to collect confidential data , such as personal information, credit card data (such as numbers, passwords, verification code, expiration date, etc.) . This content may also be accompanied by requests to download or install updates.
We can include false security warnings that arrive via email, informing about possible contamination with viruses or malware, as phishing. This email tends to victimize users who do not have great knowledge in digital security.
In its content, this same email brings a false solution to the false problem, usually involving the download of a malicious file.
Important precautions
Although it is practically impossible to prevent spam content from reaching emails, some practices can help reduce the incidence of this type of practice and avoid problems within your company:
Make your employees aware
Most spam emails are sent due to registration on websites . Companies collect our information and end up sending an absurd amount of emails to registered users. It is important that employees understand the need to avoid registering on any type of page, especially with corporate email.
The large number of unsolicited messages that are received via spam can harm worker productivity and bring security problems to the business, so this practice should be avoided. The exposure of email on the internet favors the presence of your data in lists that are bought and sold by companies illegitimately. The fewer registrations made, the more difficult it will be for your email to be used to send spam.
Beware of traps
Raffles for electronic devices, cars, gifts, among other things, are generally scams implemented just to collect information. It is important that employees behave well online and avoid providing their data to any type of website at all costs, especially when it is not directly related to activities carried out within the company.
Opt In and Opt Out
This concept refers to the permission given to send messages and notifications from a website or page to your email box. This type of form is generally found on blogs and news pages, and the user often ends up clicking automatically.
Once they obtain this consent, the website can start sending emails whenever it wants to that user and often with excessive frequency. When it comes to corporate email, this type of content can be very damaging to the business, causing unsolicited messages to arrive that take up employees' time and attention.
It is important that the Safe Internet Use Policy states that this type of practice is frowned upon and can pose a risk to productivity and the business. Employee awareness is the most important part of preventing the company from being harmed and the worker himself suffering sanctions due to inappropriate use of the corporate internet.
Opt Out, although it appears to be a solution to the problem, informs the user by decertifying that the email to which the messages are being sent is legitimate, creating greater demand for this communication channel.
Antivirus and Firewall
These resources are essential, and it is important that the company has these tools to help keep its network more secure and protect its information against cybercriminals and suspicious companies.
These tools must remain up to date to ensure that the protection offered is adequate and in line with new practices applied in the market. These updates are available for a reason, and should be performed whenever possible.
Spam marking
Although it may seem obvious, it is very important that unsolicited messages are immediately marked as spam to avoid receiving new content. Many users end up ignoring this option, but it is essential to identify the malicious or annoying nature of these messages and the damage it can cause.
This strategy helps to block future contacts and avoid overloading your email with unwanted content , maintaining productivity and focusing on activities that are really important.
Blocking websites with Lumiun Box
Blocking access to websites sent in spam emails and messages may be the best solution to prevent data leaks or internet scams from this type of attack. Lumiun Lumiun Box complete solution aimed at small and medium-sized Brazilian companies , where the control of internet access and the security of the organization's data guide its functionalities.
With an intuitive panel and no need for technical knowledge , Lumiun Box blocks websites by categories considered harmful, such as: access anonymizers, hacking, keyloggers, malware and spyware, cryptocurrency mining, phishing and online fraud .
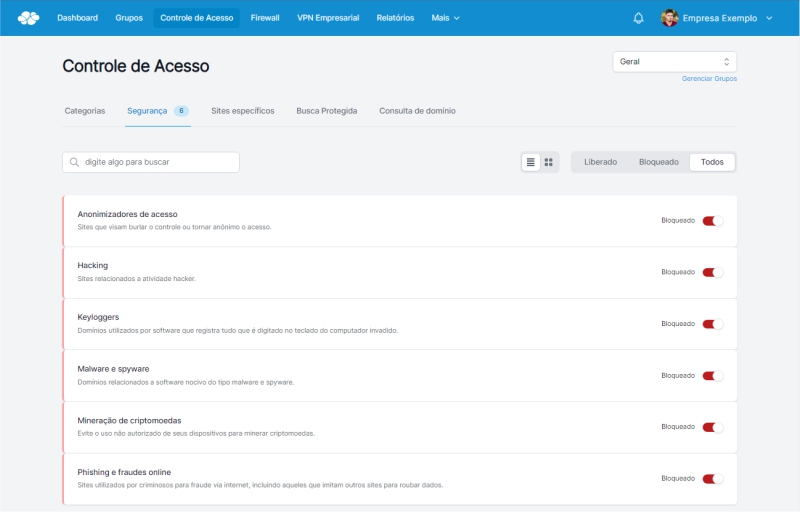
In addition to blocking websites considered harmful, Lumiun Box has the following features:
- Blocking social networks, music, video, pornography and many others;
- Business Firewall
- Business VPN
- Management of traffic and users connected to the network;
- Complete and customizable management reports
- And much more.
Take a free demo or request a no-obligation quote and see in practice how Lumiun Box can add an extra layer of protection to your company's internet .
Until later!











