One of the most effective methods used by hackers is the fake email scam. Knowing about the innocence of many users, this type of malicious attack spreads on the internet quite effectively.
According to data from the report in Brazil released by Axur, Brazil broke a record for attacks in the first quarter of 2020. There were 10,910 unique cases of phishing in the period from January 1st to March 31st in the country. This data represents an increase of 238.82% compared to the same period in 2019, when 3,220 cases were detected.
But, no panic. There are several ways to identify fake emails and protect your company's data, and that's what we'll talk about next.
What is a fake email (phishing)?

Typically, an email with a fraudulent message, using an intimidating form of communication and containing links and information in an attempt to imitate large companies (usually banks), is classified as phishing.
E-mails of this type state that failure to take action will result in the email recipient's account being blocked.
The action, in turn, is normally carried out within a (fake) website made available for access in the email sent by the criminal, and has an identical appearance to the real website.
Because it has content that generates interest in “solving” a major problem for the victim and also has an appearance extremely similar to the real thing, this type of attack is so successful.
What does phishing email look like?

With the aim of deceiving internet users, through false messages in an attempt to steal confidential information, such as access passwords, credit card data or payment of fraudulent bills, the target website for the attack is usually very well structured.
Identical to the real thing in the header, buttons, colors and logo, all exactly the same as the original.
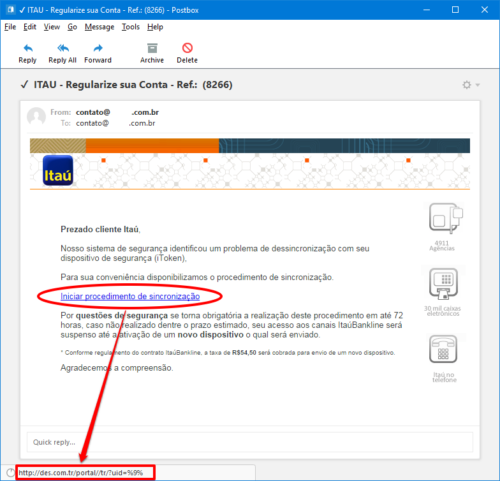
In the image below, there is an example of a phishing email supposedly from Banco Itaú, requesting synchronization of the security device.
Note that the initial text creates a sense of urgency for you to access the link below. Also note that the destination link does not make any reference to Banco Itaú.
In the video below we demonstrate how phishing received by email works, which pretends to be the PagSeguro payment service with the aim of stealing the victim's access data. First, access to the phishing site without protection is demonstrated. An attempt to access the phishing website is then demonstrated, but with the protection of an internet access control system active on the company's network.
In this way, the video presents a comparison of the effectiveness of a Phishing attack on an unprotected network and another with security and protection technology.
What questions should I ask when I receive an email like this?

Well, you may have already realized that a phishing email can easily go unnoticed by lay users. But, to the relief of many business owners concerned about this type of access by employees, some simple precautions can solve several problems, as we will see below.
- Was the email a request from me? Do not open attachments or perform actions that you have not requested.
- Is my password strong and secure ? Always keep your passwords protected, trying not to use the same password for all locations, because, if you fall for the scam, all access will be in the possession of criminals.
- Is the website URL consistent with the content or company in the email? In many phishing cases, the email address may appear legitimate, but the URL may be misspelled or the domain may be different (.com when it should be .gov). This usually immediately indicates the use of phishing.
- Do I update browser, computer and system security? Updates bring with them better protection systems, in some cases blocking access to websites considered harmful.
- Do I have a firewall and internet access control in my company? Using security systems, blocking access to harmful websites, is an “automatic” way of staying protected against attacks of this type, without the need for excessive training or care.
Having seen some ways to avoid falling for scams of this type, we can see that most of the tips involve correct behavior and user discernment. In fact, in another article here on the blog we talk more about educating employees in attacks of this type.
Don't leave your company's data security at the mercy of cybercriminals.
I hope I helped you realize the importance of protecting against phishing emails in companies.
To the next!











3 comments
Comments closed