You have probably heard of a cyber attack known as Phishing, even recently published an article that talks more about the subject. This type of attack tries to steal personal data or apply financial blows through pitfalls planted in fake emails, banners, ads, cloned websites, among other devices . In most cases, they try to go through reliable companies or known people to facilitate the blow. For this reason, it has become necessary to apply efficient measures against this type of threat , such as phishing training.
But how does this training work in practice? To help you better understand this subject, we create this exclusive material. Continue with us!
Understanding Phishing: What is the origin of this strategy?
In mid -1994, a hacker discovered a way to America online users' credit card information AOL was one of the first companies to provide internet access, having been used by numerous users around the world .
In partnership with other criminals, this hacker, passing by AOL employees, contacted users of the tool in chat rooms. To be able to stay connected, he used stolen account information in previous attacks. These stolen accounts were known as Phish.
As they were real user data, AOL administrators could not differentiate hackers from legitimate users, making this kind of approach very difficult to control. To optimize your attack, these cybercriminals have created a tool called tohell .
As he advanced and developed these traps, this type of attack became popular, and ended up known as Phishing , as he fished the information from the most lay users.
Want to know more about the concept of phishing? Take a look at this video:
Is phishing the same as spam?
Data security gained even more visibility after large companies were the target of cyber attacks . However, many users still have questions about how some attacks happen, as is the case with the phishing attack .
This shows us that phishing training for employees is essential to keeping company data protected.
A recurring question about the phishing attack is: phishing is the same as spam? The direct answer is no!
It is very common to confuse these two practices, but they have important distinctions.
Phishing is a term designated for a type of cyber attack focused on blows and fraud. One of the most common forms used by criminals who apply this type of attack is through fake emails that request confidential information for your victim.
Generally, they are disguised as real companies' emails so that users feel comfortable and end up providing their relevant data or information. This practice plants traps and use codes that allow personal data theft, bank accounts, passwords and other information.
See a very clear example below:
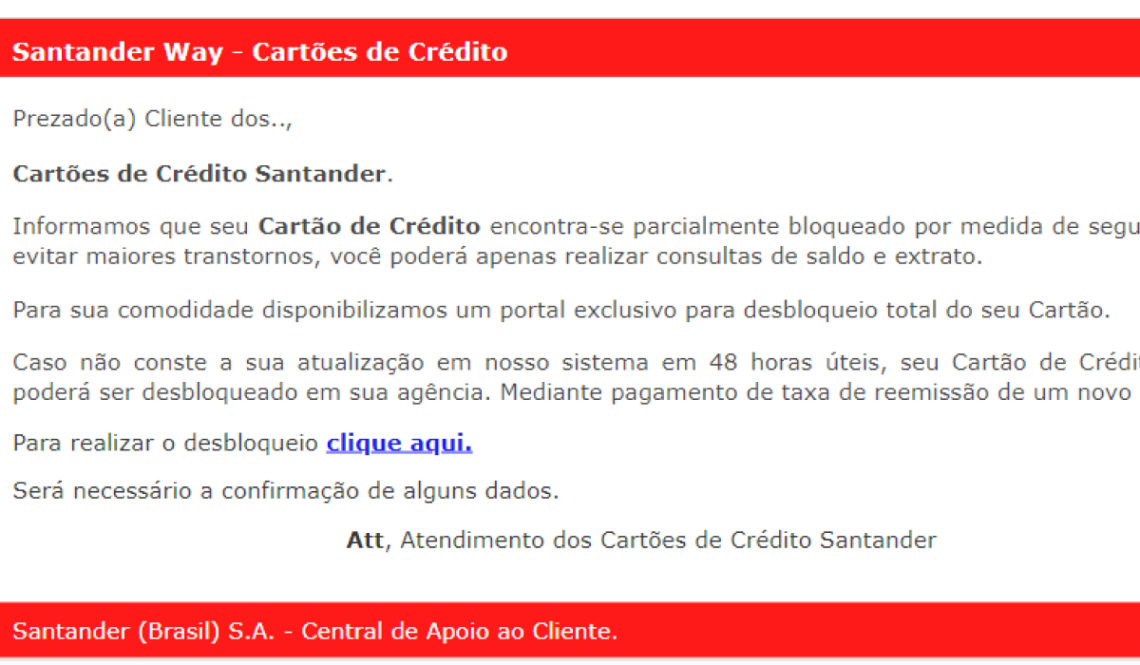
This is a fake email from Banco Santander, which presents content that catches the victim's attention, and also a link that requests personal information.
Emails of this type confuse the user and cause concern, causing distracted way, click the link and enter their data.
What risks does this type of scam have?
Phishing is a very delicate subject for the digital security of companies . This is because the safety tools used cannot identify all threats and cannot control the use profile of users in order to avoid possible traps.
This type of scam uses people's vulnerability to apply their blows so that it is very difficult to control their incidence. In this sense, phishing training represents a very important tool to combat this type of attack.
We can see how data security has become a priority in today's world. This subject has gained a lot of relevance in recent years, so much so that a new specific legislation has been created in order to increase and protect digital privacy. This law establishes rules, standards and protocols to be followed to ensure greater security for information collected and stored by companies.
By falling into a phishing blow, the company may suffer various damage , such as:
- Impact your image on the market;
- Financial losses;
- Loss of competitive positioning;
- Judicial problems;
- Exposure of your commercial strategy;
- And many other problems.
It is essential that managers understand the importance of actions focused on information security to mitigate the problems caused by data leakage. The best way to protect companies is to have a combination of technology and education , that is: to apply technological resources that help keep information safe, but also enable your employees to establish a proper internet use policy.
Is training important?
As we said earlier, as important as having technological tools to maintain data security, it is necessary to establish a phishing training process and prepare your employees to avoid this type of threat. It is important to show in a practical way what are the main points of attention to identify the phishing blow, such as:
- Generic greetings;
- Orthographic errors;
- Known but frequent contact;
- Links for personal data insertion;
- Unexpected emails with information about you that can be found on social networks;
- Threatening sentences;
- Sense of urgency;
- Unexpected awards;
- Among other suspicious behaviors.
It is impossible to predict what goals the cybercriminals have with a phishing attack. Whether downloading a malicious file within an email attachment or entering your personal information on fraudulent pages, information leakage can cause a lot of problems for a business .
Phishing training helps to reduce this risk and keep company data safely. Through this training, employees will go through a continuing education process that will help understand what phishing is in which warning signs that this attack is being performed. In this way, they will be able to determine what are the best actions to be taken in the face of this threat.
More and more companies are establishing phishing training protocols to prevent their employees' confidential information, as well as protecting their devices and preventing confidential data from being disseminated or exposed.
When it comes to cyber security, there is no way to assume that only lay people or without proper preparation are potential victims. Over the years, these attacks are increasingly effective, mainly because cybercriminals have efficient pages and divert personal data.
So if your business wants to keep your data safe and help your employees identify such attacks more easily, phishing training can be the ideal solution.
Internet access policy (block websites) can be the solution
Internet access policy can be a very useful tool for helping employees to establish a smarter usage pattern on the company. With the help of this policy, the company can make employees aware of the importance of staying outside entertainment sites, social networks and e-commerce, and the risks this type of access can cause for a business.
In this case, the concern is not only about the productivity of these workers, but also with the security of the data used by the company . To make this process even more effective, the company can also use an internet access tool to help keep these threats away from the workplace.









